What Is Cyber Security Service? Everything You Need to Know [2025]

“What Constitutes Cybersecurity Service?”. Cybersecurity service involves protecting computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks. It is also referred to as information technology security or electronic information security.
In this piece, our goal is to offer an in-depth examination of cybersecurity, encompassing aspects like threat forms, types, the advantages of cybersecurity services, and beyond. Let’s explore further!” This perspective is particularly relevant for a software development company seeking to understand and implement robust cybersecurity measures.
How Big Is The Cyber Security Industry?
The cyber security industry is growing fast due to the increasing cyber threats. It covers a wide range of areas including software, hardware, consulting, and managed services. Recent data shows that the global cyber security market was worth $161.75 billion in 2023 and is expected to reach $250.04 billion by 2030. This growth rate, averaging (CARG) 12.3% annually, highlights the urgent need and significant spending to protect digital assets across various sectors.

Image source: The Business Research Company
Looking For a Dedicated Team?
Looking to fortify your manufacturing operations with top-tier cybersecurity services? Look no further than Savvycom! With over 15 years of excellence in IT development, Savvycom specializes in providing tailored cyber security solutions to meet your industry’s unique needs. Partner with us for expert cyber security consulting, as Asia’s premier IT outsourcing company, and unlock the power of innovative technology to safeguard your manufacturing processes. Together, let’s elevate your security measures and propel your business to new heights of success!
Typical Hazards and Dangers Encountered by Companies

As technology evolves, so do the myriad threats in cyberspace
Cyber threats today are evolving rapidly, posing different challenges compared to just a few years ago. With the ever-changing cyber threat landscape, organizations must adapt to safeguard against the sophisticated tools and techniques employed by cybercriminals both now and in the future.
Hacking
Hacking, at its worst, means breaking into computer systems without permission to steal valuable information. This can lead to serious problems like data theft or even controlling systems for harmful purposes. Hackers have different reasons for doing this and they use advanced methods to bypass security measures. When they succeed, it can cause big financial losses and damage reputations. That’s why strong cybersecurity is crucial to prevent these kinds of attacks.
Malware
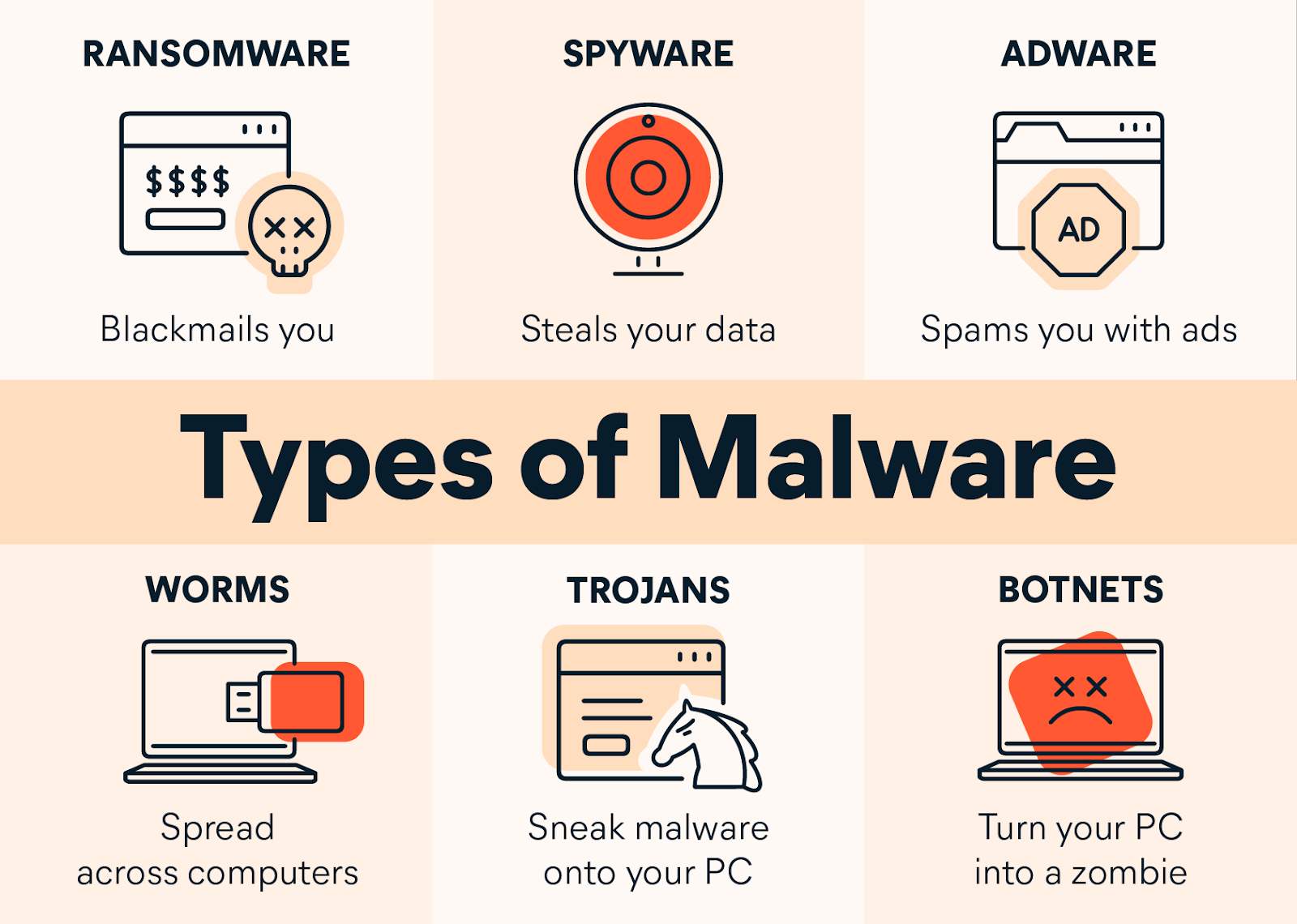
Types of popular Malware – Image source: Avast
Malware, a sneaky type of software, aims to sneak into and harm computer systems. It includes viruses, worms, trojans, ransomware, and spyware, causing big problems for both people and groups. These bad programs can mess up how things work, take important information, or get into networks without permission. When malware strikes, it can cause big trouble like losing data, losing money, or making security weaker. Keeping up with and fighting malware is super important for keeping things safe online as threats keep changing.
Phishing
Phishing is a sneaky cyber trick where bad guys pretend to be someone they’re not, like a real company, usually through emails. It’s a common way for cybercriminals to fool people into giving away personal stuff, like passwords or credit card numbers. Phishing scams are getting fancier, which makes them tougher to spot and scarier. Since they’re hitting all kinds of businesses, it’s super important to know how to spot them to keep your info safe and your online world secure.
Social Engineering
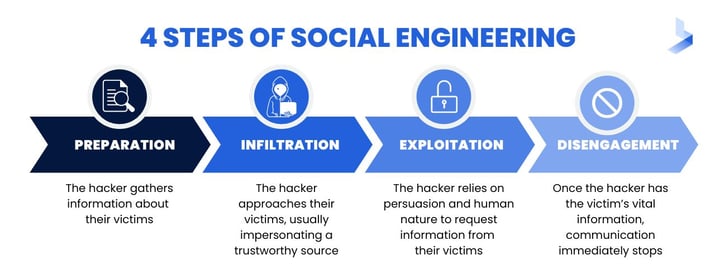
Simulate 4 attack steps of Social engineering
Social engineering, demonstrated in notable cyber attacks like the $100 Million Google and Facebook Spear Phishing Scam, the Sophisticated US Department of Labor Phishing Attack, and the Belgian Bank “Whaling” Attack, involves manipulating people to gain access to confidential information or commit fraudulent activities.
Social engineering is a sophisticated method of tricking individuals by first thoroughly researching them. It’s akin to when malicious actors create highly convincing emails tailored specifically to the recipient, leveraging personal information to obtain secrets or manipulate individuals into engaging in unsafe actions. The alarming aspect of social engineering is its independence from advanced technology; instead, it exploits human vulnerabilities. This is why combating social engineering is crucial for ensuring online safety.
Distributed Denial-of-service (DDoS) Attacks
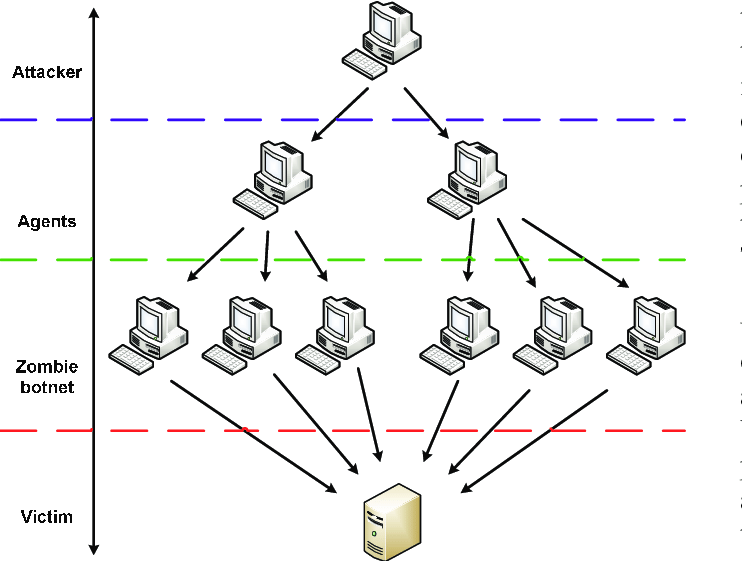
How a DDoS attack works
Denial-of-Service (DDoS) attacks are like digital tsunamis. They flood networks and servers with a massive wave of traffic, making it nearly impossible for regular folks like us to use online services. These attackers hijack countless systems, forming a zombie army known as a botnet, to unleash this flood.
When a DDoS attack hits, it’s like a blackout – services can go down for a short while or even for ages, disrupting businesses and inconveniencing everyone. So, they’re not just irritating glitches; they’re a major security headache that requires solid defense plans to keep our online world up and running smoothly.
Advanced Persistent Threats (APT)
Advanced Persistent Threats (APTs) are essentially like stealthy cyber infiltrators. They’re crafted by skilled groups, often comprising experienced cybercriminals with substantial financial backing, aiming to pilfer crucial data or stir up chaos within networks. APTs are notorious for their cunning tactics, high level of sophistication, and substantial resources at their disposal.
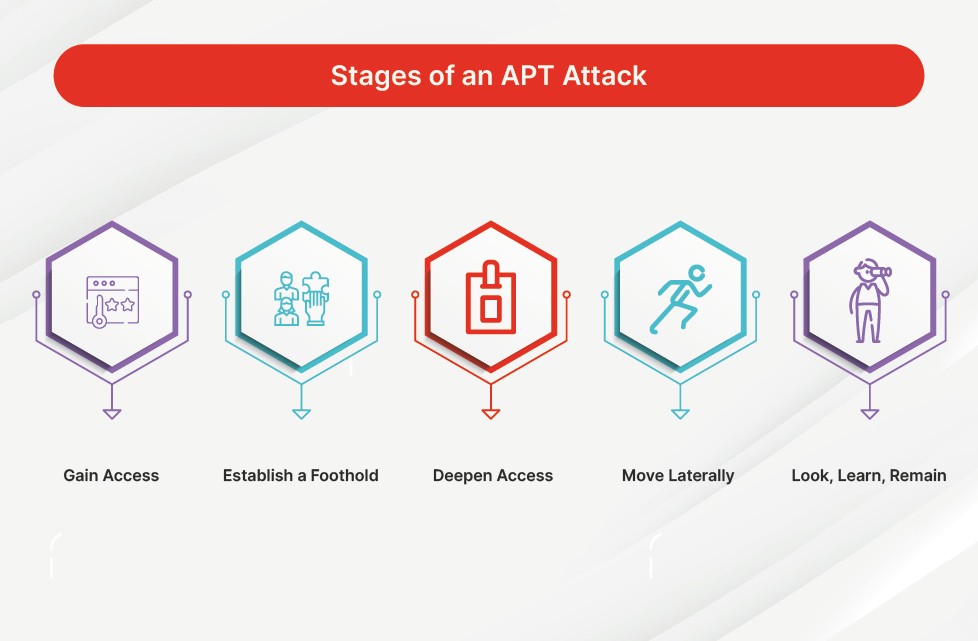
Stages of an APT Attack – Image source: Fortinet
Typically, they begin by hoodwinking individuals or exploiting system vulnerabilities. Then, they employ malware to burrow deeper into the network, quietly navigating its pathways to stealthily extract valuable information, posing a significant challenge to cybersecurity measures. Some of their attack activities can be mentioned as:
- Intellectual property theft (e.g., trade secrets or patents)
- Compromised sensitive information (e.g., employee and user private data)
- The sabotaging of critical organizational infrastructures (e.g., database deletion)
- Total site takeovers.
Man-in-the-middle (MitM) Attacks
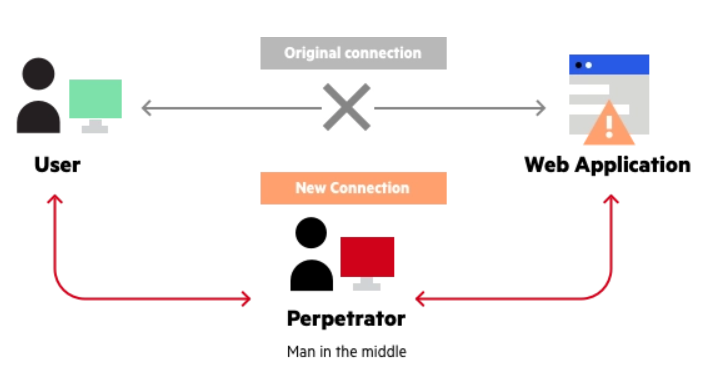
Example of MitM attacks – Image source: Imperva
Man-in-the-middle attacks are a major worry in the world of security. In these attacks, the bad guys sneak themselves into a conversation between two parties to steal or tamper with the data being exchanged. It’s a sneaky move that lets them snatch up sensitive information like login credentials, account details and credit card numbers, and they can even slip harmful stuff into the conversation. MitM attacks can happen in lots of different situations, from someone on public Wi-Fi to big companies passing around important data. Protecting against these attacks means using secure communication methods like HTTPS, keeping a close eye on things, and setting up strong security to catch and stop any unauthorized snooping.
SQL Injection
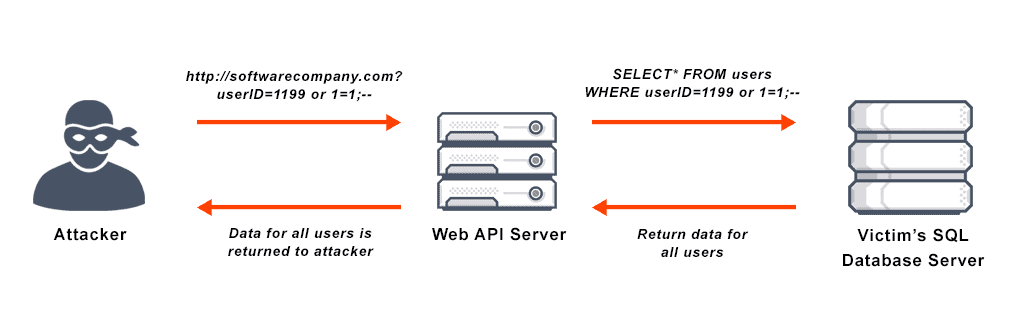
SQL injection attack steps – Image source: GiftHub
SQL injection is a common cyber threat that messes with a web application’s database by injecting code. Bad actors take advantage of weaknesses to run commands they shouldn’t, getting into sensitive data, messing with it, or even taking control of the whole database. This method can mess up the trustworthiness, secrecy, and accessibility of data, putting any application that talks to SQL databases at risk. So, it’s super important to guard against SQL injection by coding carefully, using things like prepared statements and stored procedures.
Benefits Of Cybersecurity Services

Unlocking the Potential of Cybersecurity Services
We’ve covered some typical cyber-attacks. In today’s digital landscape, setting up a network firewall for security is crucial. That’s why, in this section, we’ll discuss the top three advantages of having network protection in place.
Protection Against Data Breaches
The threat of cyber attacks is a major concern for businesses globally. Data breaches can result in the loss of crucial assets like trade secrets and financial records, making companies susceptible to exploitation by cybercriminals. This could lead to expensive legal disputes. To address these risks, taking proactive steps is crucial. Establishing strong cybersecurity protocols is key to protecting sensitive information and preserving trust with stakeholders.
By focusing on prevention through rigorous security measures like encryption, multi-factor authentication, and regular security assessments, organizations can bolster their defenses against potential breaches, thus safeguarding the integrity and confidentiality of their data.
Increased Privacy and Security
Protecting sensitive data is crucial for businesses to uphold trust and integrity with their customers. Implementing strong cybersecurity measures is vital to safeguard both the company’s and its customers’ information. By integrating encryption, access controls, and other advanced security protocols, organizations can greatly improve the protection of their digital assets. These actions not only reduce the risk of data breaches but also show a dedication to prioritizing customer privacy and establishing a robust business environment. With cybersecurity as a fundamental part of their operations, businesses can inspire confidence in their stakeholders and promote sustainable growth in today’s interconnected world.
Improved Brand Reputation and Customer Trust
Brand reputation and customer trust are priceless assets for any business. By implementing strong cybersecurity technologies, not only are networks, data, and applications protected from unauthorized access, but they’re also constantly monitored for any suspicious activities. This vigilance is essential in thwarting attacks that may compromise or steal data, guaranteeing that sensitive information is accessible only to authorized individuals. Taking this proactive stance on cybersecurity not only strengthens a company’s defenses but also boosts its reputation, reassuring customers that their data is secure.
6 Types Of Cybersecurity Services
In this section, we’ll delve into the various types of network cybersecurity services, exploring their purposes and the advantages they offer. Cybersecurity encompasses a wide array of elements, which can be categorized into six primary pillars:
Network Security

Network security involves protecting computer networks from unauthorized access or malicious activities, ensuring data confidentiality, integrity, and availability
Protecting a company’s digital assets from cyber threats is crucial. Network security system is the cornerstone of this protection, focusing on safeguarding network infrastructure and traffic from unauthorized access, intrusion, and exploitation.
Cyberattacks predominantly target networks, underscoring the necessity for robust network security solutions. These solutions incorporate various controls like:
- Data Loss Prevention (DLP): DLP stops sensitive data from being lost or stolen by monitoring and controlling its movement across devices and networks.
- Identity Access Management (IAM): IAM manages who has access to what in your organization’s IT systems, ensuring security and compliance.
- Network Access Control (NAC): NAC regulates network access based on security policies, verifying users and devices before granting entry to prevent unauthorized access.
- Next-Generation Firewall (NGFW): NGFW combines traditional firewall features with advanced threat detection to protect against sophisticated cyber threats.
In addition, advanced technologies like Intrusion Prevention System (IPS), Next-Gen Antivirus (NGAV), Sandboxing, and Content Disarm and Reconstruction (CDR) offer multi-layered threat prevention. Furthermore, network analytics, threat hunting, and automated Security Orchestration and Response (SOAR) technologies play crucial roles in bolstering network security.
Cloud Security

Protecting data and applications in cloud computing environments from cyber threats
As more businesses turn to cloud computing, keeping cloud-based data and applications safe is crucial. Cloud security involves defending data, applications, and infrastructure stored in cloud setups from cyber threats.
A strong cloud security strategy brings together cybersecurity solutions, controls, policies, and services to protect the entire cloud deployment from potential attacks. Although many cloud providers provide security solutions, they might not always meet the rigorous security standards required by enterprises. This often means adding extra third-party solutions to reduce the risks of data breaches and targeted attacks.
Thus, creating a successful cloud security plan demands a proactive and thorough approach to tackle the distinct security issues that arise in cloud environments.
Endpoint Security
Protecting individual devices from cyber threats
Endpoint security is a vital part of cybersecurity, focusing on securing every device that connects to a network to prevent unauthorized access and other risky actions at these entry points. It’s all about protecting individual devices like computers, mobile devices, and servers from malicious activities and breaches.
The zero-trust security model highlights the importance of creating small segments around data, underscoring why endpoint security is especially crucial, particularly for mobile workers.
Endpoint security solutions typically include controls for data and network security, along with advanced threat prevention measures like anti-phishing and anti-ransomware. Additionally, they often feature technologies for forensic analysis, such as endpoint detection and response (EDR) solutions.
Mobile Security

Protecting smartphones and tablets from cyber threats
Ensuring mobile security is essential for safeguarding both personal and business information stored on smartphones, tablets, and other mobile devices. This means protecting these devices, along with their applications and data, from various threats like malware, data breaches, and unauthorized access.
Despite their importance, mobile devices are often overlooked in terms of security, which can expose businesses to significant risks. These risks stem from the access these devices have to corporate data, leaving them vulnerable to threats like malicious apps, zero-day attacks, phishing, and Instant Messaging (IM) attacks.
Implementing mobile security measures is crucial to thwarting such threats and bolstering the security of operating systems. These measures also work to protect devices from rooting and jailbreaking attempts. Additionally, integrating with Mobile Device Management (MDM) solutions ensures that only compliant devices can access corporate assets, adding an extra layer of protection.
IoT Security
Ensuring the security of Internet of Things (IoT) devices has become a critical concern. With the widespread adoption of these devices, prioritizing IoT security is a must. Safeguarding both the devices themselves and the networks they connect to is vital in order to thwart unauthorized access and prevent data breaches.
Despite the convenience and efficiency that IoT devices offer, cybercriminals also introduce new cyber threats. Cybercriminals exploit vulnerabilities in IoT devices to gain access to sensitive information or to launch cyber-attacks.
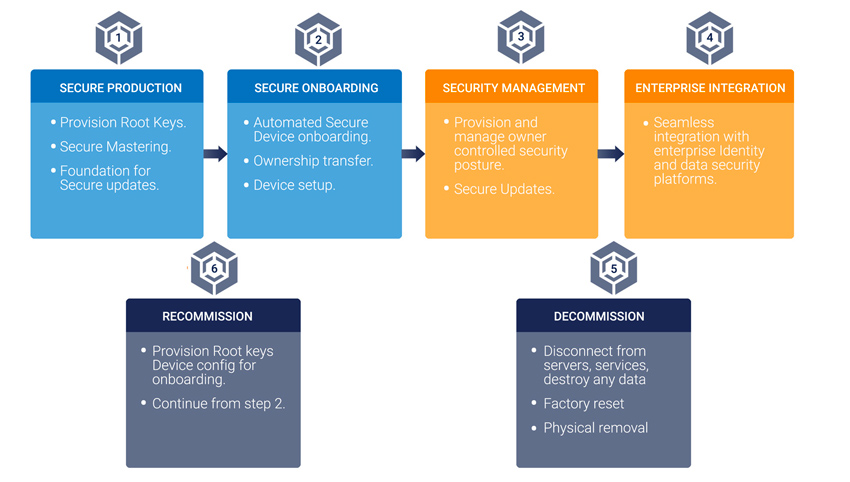
IOT security steps – Image source: EPS Programming
To address these risks, implementing robust authentication and encryption protocols, regularly updating device credentials, and deploying protections against DDoS attacks are essential measures. Additionally, emerging security techniques such as behavioral analysis and enhanced encryption standards are gaining traction as forward-thinking security solutions.
Application Security
Application security entails enhancing the safeguarding of software against a multitude of risks and vulnerabilities, spanning from clandestine cyber threats to potential weaknesses that hackers could exploit. This aspect is particularly critical for web applications, given their direct connection to the internet, rendering them susceptible targets for cyber-attacks. This underscores the significance of robust software development services in fortifying application security measures.
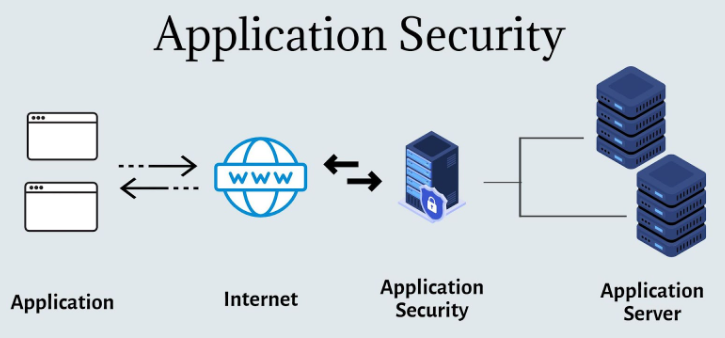
Ways Application Security works – Image source: Atatus
Since 2007, the Open Web Application Security Project (OWASP) has been keeping tabs on the top 10 threats to web application security. These threats include things like injection attacks, broken authentication, misconfigurations, and cross-site scripting. By focusing on application security, businesses can effectively tackle these threats head-on, preventing malicious attacks outlined in the OWASP Top 10 and keeping their applications and APIs safe from harm.
How Much Do Cyber Security Companies Charge?
Computer security and cybersecurity services don’t come with a fixed price tag. The cost varies depending on several factors like what exactly you need, how big and complex your business is, and how much protection you want. When you hire a cybersecurity service firm, they might charge you a set amount for everything or they might charge you based on things like how many people or devices they need to protect for you.
For example, if you’re running a small network, monitoring services might cost you anywhere from $100 to $500 per month. But if your network is bigger, expect to pay between $500 and $2,000 per month. And if you need specialized cybersecurity services like detecting breaches, you might pay an hourly rate ranging from $150 to $199.
It’s really important for businesses to carefully think about what they need and how much they can spend when they’re choosing a cybersecurity service provider. That way, they can make sure they get the protection they need without blowing their budget.
Bottom Line: What Is Cybersecurity Service?
In the modern digital landscape, cybersecurity isn’t just an optional extra—it’s essential. With the rising tide of cyber threats, businesses across all sectors and scales must prioritize investing in strong cybersecurity measures to safeguard their valuable data and keep their operations running smoothly. By gaining insight into the diverse array of cyber threats and the range of cyber security outsourcing services on offer, businesses can adopt a proactive stance toward protecting their digital assets. We trust that our article will provide clarity on the topic of cybersecurity services. Best of luck!
Savvycom – Your Trusted Tech Partner
Transforming Manufacturing with Cutting-Edge Cyber Security Solutions: Savvycom, Asia’s Premier IT Outsourcing Provider, has been at the forefront of digital innovation since 2009. Leveraging our expertise, we specialize in developing top-tier cyber security software tailored to meet your needs. From robust learning platforms to interactive tools, we provide comprehensive solutions to enhance teaching and learning experiences. Partner with us to revolutionize education through technology.
Savvycom is right where you need. Contact us now for further consultation:
- Phone: +84 24 3202 9222
- Hotline: +84 352 287 866 (VN)
- Email: [email protected]


