Cybersecurity for Small Businesses: Safeguarding Your Business in the Digital Age
In the ever-evolving digital landscape, cybersecurity for small businesses is more important than ever. Many small business owners mistakenly believe that hackers target only large enterprises, but the statistics tell a different story. According to the Verizon Data Breach Investigations Report, 43% of all cyberattacks are aimed at small businesses. Unfortunately, these organizations often lack the necessary defenses, making them attractive to cybercriminals. Shockingly, 60% of small businesses that experience a cyberattack close their doors within six months
Why are small businesses increasingly under siege? Hackers view these organizations as “soft targets” because they typically lack advanced security measures. Compounding the issue, many small businesses are unaware of the cybersecurity risks they face. This article provides an in-depth analysis of the threats, real-world cases, and solutions to ensure that your business stays protected in a digital-first world.
The Rising Impact of Cyberattacks on Small Businesses
Financial Fallout: When Cyberattacks Drain Your Resources
Cyberattacks are not just IT problems—they are existential threats that can cripple small businesses financially. According to the IBM Cost of a Data Breach Report 2023, the average cost of a data breach globally is $4.45 million. While large companies have the financial reserves to weather such losses, small businesses operate on tight budgets and limited cash flow, making recovery exceedingly difficult.
Image source: Syteca
In addition to paying ransom demands or recovering stolen data, businesses incur other expenses such as downtime, legal fees, and lost revenue. Even a small-scale attack can disrupt operations for days or weeks, resulting in missed sales opportunities and unmet customer expectations.
A retail chain in Texas learned this lesson the hard way when hackers encrypted its sales database. The attackers demanded $25,000 in Bitcoin, a sum the business reluctantly paid to avoid losing its entire inventory and customer data. However, despite paying the ransom, the business lost an additional $100,000 in operational revenue due to weeks of downtime and reduced customer confidence.
This scenario highlights a critical issue: Paying the ransom often does not guarantee a smooth recovery. Businesses must also invest in rebuilding systems, repairing relationships with customers, and protecting their brand reputation.
Erosion of Customer Trust: A Hidden Cost
Cybersecurity for small businesses is not only about protecting systems and data—it’s also about protecting relationships. Customers place immense trust in businesses, expecting their personal information to remain secure. When that trust is broken, the repercussions extend beyond immediate financial loss to long-term brand damage.
A Verizon report revealed that 28% of small businesses that suffer data breaches struggle to retain their customers afterward. Customer churn is especially damaging for small businesses that rely on repeat business and word-of-mouth referrals to grow. For these companies, rebuilding lost trust can be a slow, costly process.
A small law firm in New York suffered a phishing attack that compromised sensitive client records. Even after successfully recovering the stolen data, several clients severed ties with the firm, resulting in both financial losses and reputational damage. In such cases, trust—an invaluable asset—becomes nearly impossible to restore.
Get in touch with Savvycom for a free consultation. We’ll help you decide on next steps, explain how the development process is organized, and provide you with a free project estimate.
The Most Common Cyber Threats Faced by Small Businesses
1. Phishing and Social Engineering Attacks: The Gateway to Data Breaches
Phishing and social engineering attacks exploit human psychology rather than technological vulnerabilities. In phishing schemes, cybercriminals send deceptive emails or text messages that trick employees into divulging passwords or clicking on malicious links.
Phishing is responsible for 90% of all data breaches, according to a report by Cisco. These attacks are particularly dangerous for small businesses with limited cybersecurity training, as employees may lack the skills to identify fraudulent communications.
Case in Point: A Phishing Attack Gone Wrong
A small accounting firm in California fell victim to a phishing attack when an employee unknowingly opened a fake invoice email. The malware embedded in the email gave hackers access to the firm’s financial systems, compromising confidential client data. As a result, the business incurred penalties for non-compliance with PCI DSS standards, along with losing several high-value clients.
2. Ransomware: Holding Businesses Hostage
Ransomware attacks involve hackers encrypting a business’s files, rendering them inaccessible until a ransom is paid. Unfortunately, paying the ransom does not always lead to a resolution—51% of ransomware victims lose data even after paying. Small businesses, which may not have robust backup systems in place, often find themselves forced to comply with the attackers’ demands.
Ponemon Institute reports that ransomware incidents have been rising steadily, with small businesses becoming a frequent target. Attackers know that smaller companies are more likely to pay quickly to minimize downtime, especially if they lack contingency plans.
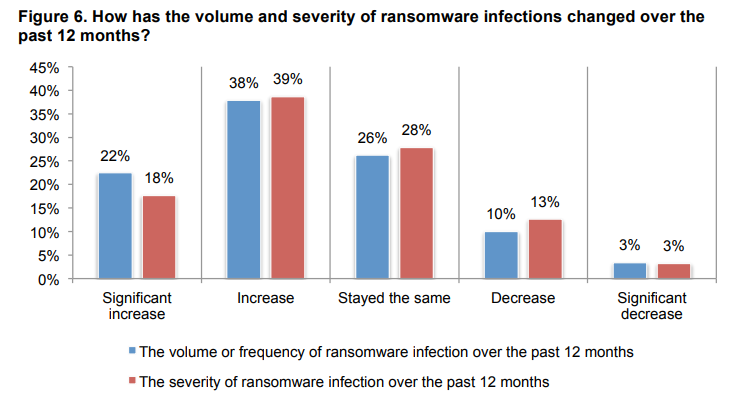
Image source: Ponemon Institute
Critical Cybersecurity Measures for Small Businesses
1. Network Security: The Foundation of Your Defense
Every business, no matter the size, should have a firewall to block unauthorized access and a VPN to encrypt data transmissions. However, network security goes beyond basic tools—continuous monitoring is essential to detect and neutralize threats in real time.
-
Savvycom’s MSSP solutions offer intrusion detection systems (IDS) and threat monitoring, providing small businesses with advanced protection against hackers. SIEM monitoring aggregates and analyzes security data from across your network, enabling faster threat detection and response.
-
Network Segmentation: By separating sensitive systems from general networks, businesses can contain potential breaches and limit damage.
2. Endpoint Security: Protecting Devices in the Age of Remote Work
With remote work becoming more prevalent, endpoint security—ensuring that laptops, smartphones, and tablets are secure—is paramount. Mobile device management (MDM) tools help businesses control access to sensitive information, even on employee-owned devices.
A digital marketing agency with remote employees implemented MDM software to enforce device encryption and ensure that only authorized apps were used. This proactive approach prevented a malware infection when a device was lost, sparing the agency from potential data exposure and reputational harm.
3. Data Backup and Recovery: Your Lifeline in a Crisis
Backing up critical data regularly ensures that businesses can recover quickly after an attack or system failure. Backup solutions should be automated, tested frequently, and stored both on-site and in the cloud to guarantee availability.
-
Savvycom’s disaster recovery cybersecurity services ensure that businesses can restore operations with minimal downtime after an incident.
-
Tip: Conduct periodic disaster recovery drills to ensure all employees are familiar with recovery procedures.
4. Employee Training: Building a Human Firewall
Employees are often the weakest link in any types of cybersecurity. Even the most secure systems can be compromised by a simple mistake, such as clicking on a phishing link. Regular security awareness training and phishing simulations can empower employees to identify threats and take appropriate action.
- Tip: Encourage employees to report suspicious emails promptly, creating a proactive security culture within the organization.
Compliance and Legal Considerations for Small Businesses
Compliance with data privacy regulations is non-negotiable, even for small businesses. Failing to meet regulatory standards can result in hefty fines, legal action, and reputational damage.
1. GDPR: Protecting European Customers’ Data
The General Data Protection Regulation (GDPR) requires businesses to obtain explicit consent before collecting personal data from EU citizens. Non-compliance can result in penalties of up to €20 million or 4% of global turnover, whichever is higher. Small businesses that operate internationally must understand and comply with these requirements to avoid fines.
2. PCI DSS: Securing Payment Transactions
Businesses that process credit card payments must adhere to PCI DSS standards to protect cardholder data. This includes encrypting payment information and implementing secure payment gateways. Non-compliance can lead to fines, increased transaction fees, or the loss of the ability to process credit card payments.
3. HIPAA: Protecting Healthcare Data
Healthcare businesses are subject to HIPAA regulations, which mandate strict protections for patient data. Even small healthcare providers must implement security measures to prevent unauthorized access to patient information.
- Savvycom’s compliance consulting services help businesses navigate complex regulations and implement cybersecurity best practices to avoid penalties.
Building a Comprehensive Cybersecurity Plan for Small Businesses
Creating a robust cybersecurity for small businesses is to mitigate risks and ensures operational continuity even in the face of cyber threats. A strong cybersecurity plan must be proactive, encompassing risk assessment, policy development, incident response planning, and continuous monitoring.
Step 1: Conduct a Risk Assessment
The first step in any cybersecurity strategy is to identify critical business assets and assess the risks they face. This allows businesses to prioritize their resources on areas that need the most protection. A retail business might focus on securing its Point-of-Sale (POS) system since compromised payment data can expose the company to fraud and PCI DSS violations.
- Healthcare providers will prioritize the security of patient records, ensuring compliance with HIPAA regulations.
By understanding the business’s vulnerabilities and mapping out potential attack vectors, companies can implement tailored security solutions. Conducting regular risk assessments ensures that businesses remain responsive to evolving threats.
Step 2: Develop Security Policies and Procedures
Policies and procedures form the backbone of a successful cybersecurity framework. These internal rules provide employees with clear guidance on how to manage passwords, handle sensitive data, and report suspicious activities.
Best Practices for Security Policy Development
- Password Management Policies:
- Require strong passwords (minimum 12 characters with symbols and numbers).
- Implement password expiration policies to ensure periodic changes.
- Access Control Policies:
- Use role-based access control to limit data access to employees on a need-to-know basis.
- Incident Reporting:
- Encourage employees to report cybersecurity incidents promptly and without fear of repercussions.
- Tip: Integrate Multi-Factor Authentication (MFA) across all systems to add an extra layer of protection. This reduces the chances of a breach, even if passwords are compromised.
Step 3: Implement an Incident Response Plan
A well-defined incident response plan (IRP) ensures that your business can act swiftly in case of a cyberattack. The IRP outlines steps to contain, mitigate, and recover from attacks, reducing potential damage.
Core Elements of an Incident Response Plan
- Preparation: Train employees to recognize threats and report them immediately.
- Detection and Analysis: Use monitoring tools to detect unusual behavior and assess the scope of incidents.
- Containment: Isolate affected systems to prevent further spread.
- Eradication and Recovery: Remove malicious files and restore operations using backups.
- Post-Incident Review: Conduct a review to identify areas for improvement and update the response plan accordingly.
A quick response prevented a ransomware attack from spreading across a small business’s network. By immediately isolating the affected systems, the company avoided paying ransom demands and restored its systems using backups.
Step 4: Continuous Monitoring and Improvement
Cybersecurity for small businesses is not a one-time effort but an ongoing process. Regular audits, penetration testing, and vulnerability scans help businesses stay ahead of evolving threats.
- Audits: Review security measures periodically to ensure compliance with regulations and identify gaps.
- Penetration Testing: Simulate attacks to test your defenses and uncover weaknesses.
- Software Updates: Ensure all systems receive regular patches to close known vulnerabilities.
Looking For a Trusted Tech Partner?
We’ll help you decide on next steps, explain how the development process is organized, and provide you with a free project estimate.
Budgeting for In-house vs. Outsourcing Cybersecurity for Small Businesses
Cost-Effective Cybersecurity Tools for Small Businesses
Small businesses often face budget constraints, making it crucial to start with affordable cybersecurity tools. Implementing effective cybersecurity for small businesses is essential for safeguarding sensitive information and ensuring operational continuity. Here are some cost-effective cybersecurity tools that can significantly enhance cybersecurity for small businesses:
-
Bitdefender: This reliable antivirus program offers strong malware protection, helping to secure systems against various cyber threats. It’s an excellent choice for cybersecurity for small businesses looking for effective antivirus solutions.
-
LastPass: As a password manager, LastPass assists small businesses in securely storing and generating strong passwords. Implementing such a tool is vital for improving overall cybersecurity for small businesses.
-
Cloud Backup Solutions: Regularly backing up essential data is critical for protecting against ransomware and data loss. Utilizing cloud backup solutions is a proactive step in ensuring robust cybersecurity for small businesses.
-
Cyber Insurance: Investing in cyber insurance can help businesses recover from financial losses resulting from cyber incidents. This form of insurance is an essential aspect of comprehensive cybersecurity for small businesses.
While these tools provide a foundational level of protection, many small businesses still struggle with the resources necessary to maintain in-house cybersecurity teams. It’s important for small businesses to prioritize cybersecurity for small businesses and consider both tools and strategies to enhance their defenses against cyber threats.
Outsourcing to an MSSP: A Strategic Choice
For more advanced cybersecurity for small businesses, outsourcing to a Managed Security Service Provider (MSSP) like Savvycom is often the best option. MSSPs provide access to enterprise-level security tools such as SIEM monitoring, threat intelligence, and incident response services, all at a predictable monthly cost.
Benefits of Outsourcing to Savvycom
- Access to Expertise: Gain access to cybersecurity professionals without hiring in-house staff.
- Cost Savings: Reduce costs with predictable monthly fees for advanced security services.
- 24/7 Threat Monitoring: MSSPs monitor systems continuously, providing real-time alerts and responses.
Savvycom – a leading software development company – offers comprehensive MSSP solutions tailored to the unique needs of small businesses, ensuring protection without stretching budgets.
Emerging Trends and Threats in Cybersecurity
The cybersecurity landscape evolves rapidly, with new threats emerging every day. Small businesses need to stay informed and proactive to protect themselves.
1. Ransomware-as-a-Service (RaaS)
RaaS platforms allow non-technical attackers to launch ransomware attacks by purchasing ready-made malware kits on the dark web. This trend increases the frequency of attacks, especially targeting small businesses that lack sophisticated defenses.
- Tip: Regular data backups and offline storage can mitigate the impact of ransomware attacks.
2. AI-Powered Threat Detection
Artificial intelligence (AI) and machine learning are transforming cybersecurity. These tools analyze large datasets to detect unusual activity and predict threats, providing real-time protection. AI-enabled security solutions can identify and block phishing emails before they reach employees’ inboxes, reducing the likelihood of human error.
3. Cloud Security Risks
As more businesses move to cloud environments, securing cloud platforms becomes critical. Misconfigured cloud services often expose businesses to data breaches. Multi-layered security protocols are essential to protect cloud-based data. Savvycom’s cloud security solutions help businesses secure their cloud platforms by configuring settings correctly and monitoring for unauthorized access.
4. Zero Trust Cybersecurity Framework
The zero trust implementation ensures that no user or device, even within the organization, is automatically trusted. This framework reduces the risk of insider threats and external attacks.
- Practical Tip: Implement micro-segmentation to control access to specific parts of your network, minimizing potential damage from breaches.
Why Choose Savvycom for Cybersecurity?
With over 15 years of experience, Savvycom offers tailored cybersecurity outsourcing services that meet the needs of small businesses. From pentesting and red team operations to incident response and compliance consulting, Savvycom provides comprehensive services to protect businesses from evolving threats.
- Proactive Protection: Continuous monitoring and threat detection keep businesses secure in real-time.
- Regulatory Compliance: Savvycom’s compliance consulting ensures adherence to industry standards like GDPR and HIPAA.
- Customized Solutions: TTP cybersecurity, MSP cybersecurity, MSP vs MSSP services, zero trust security are tailored to meet the specific requirements and budgets of small businesses.
Partnering with Savvycom – one of top cybersecurity companies – allows small businesses to focus on growth, knowing their cybersecurity needs are in expert hands.
Conclusion
Investing in cybersecurity for small businesses is no longer optional—it’s essential. By conducting risk assessments, developing security policies, implementing incident response plans, and monitoring systems continuously, small businesses can stay protected. Outsourcing to expert cybersecurity service providers like Savvycom ensures advanced security without straining internal resources.
Don’t wait until a breach occurs. Contact Savvycom today to explore how our tailored cybersecurity solutions can safeguard your business in the digital era and position you for long-term success.
Tech Consulting, End-to-End Product Development, Cloud & DevOps Service! Since 2009, Savvycom has been harnessing digital technologies for the benefit of businesses, mid and large enterprises, and startups across the variety of industries. We can help you to build high-quality software solutions and products as well as deliver a wide range of related professional services.
Savvycom is right where you need. Contact us now for further consultation:
- Phone: +84 24 3202 9222
- Hotline: +1 408 663 8600 (US); +612 8006 1349 (AUS); +84 32 675 2886 (VN)
- Email: [email protected]