10 Reasons Why Cyber Security Is Important: A Comprehensive Guide for 2026
In today’s digital-first world, cyber security has evolved from a nice-to-have to a business-critical necessity. With cybercrime projected to cost the world $10.5 trillion annually by 2025 and global cybersecurity spending expected to reach $212 billion in 2025, understanding why cyber security is important has never been more crucial for businesses of all sizes.
Understanding Cyber Security in the Modern Business Landscape
Cyber security encompasses the comprehensive practices, technologies, and measures designed to protect networks, computers, and data from unauthorized access, misuse, and damage. It involves multiple layers of protection including encryption, authentication, intrusion detection, and advanced threat monitoring systems.
For businesses operating in today’s interconnected digital economy, cyber security serves as the foundation for:
- Data protection and privacy compliance
- Business continuity and operational resilience
- Customer trust and brand reputation
- Financial stability and growth sustainability
The Top 10 Reasons Why Cyber Security Is Important
1. Protecting Sensitive Personal and Business Data
The Stakes Have Never Been Higher
The average cost of a data breach reached an all-time high of $4.88 million in 2025, a 10% increase from 2023. This staggering figure represents more than just financial loss—it encompasses the devastating impact on customer trust, regulatory penalties, and long-term business viability.
Key Data Protection Priorities:
- Personal Information: Social security numbers, addresses, phone numbers, and family details
- Financial Data: Banking information, credit card details, and transaction histories
- Health Records: Medical histories, insurance information, and treatment plans
- Business Intelligence: Customer databases, employee records, and proprietary research
Real-World Impact: Healthcare organizations face particularly severe consequences, with 54% of healthcare IT professionals believing their organizations are vulnerable to ransomware attacks. The healthcare sector’s average data breach cost exceeds $10 million, making robust cyber security measures essential for patient safety and regulatory compliance.
2. Preventing Identity Theft and Financial Fraud
The Growing Threat Landscape
Identity theft has evolved into a sophisticated criminal enterprise, with cybercriminals using advanced techniques including deepfakes, social engineering, and AI-powered attacks. 97% of companies are reporting GenAI security issues and breaches, highlighting how emerging technologies create new vulnerabilities.
One increasingly prevalent example is iCloud storage scams, where fraudsters send convincing emails or text messages appearing to come from Apple, warning users that their storage is full or their account has been compromised. Victims who click on these malicious links are directed to fake login pages designed to harvest Apple ID credentials, credit card information, and personal data—potentially giving attackers access to photos, documents, and even the ability to lock users out of their own devices.
Modern Identity Protection Strategies:
- Multi-Factor Authentication (MFA): Adding layers beyond passwords
- Biometric Security: Fingerprint, facial recognition, and behavioral analysis
- Continuous Monitoring: Real-time detection of suspicious activities
- Zero Trust Architecture: Verifying every user and device before granting access
Financial Impact: Small businesses face particularly severe consequences, with 60% of small businesses ranking cybersecurity threats as a top concern. The average cost for SMBs with fewer than 500 employees reaches $2.98 million per incident.
3. Ensuring Secure Online Transactions and E-commerce
The Digital Economy’s Foundation
As e-commerce continues to dominate global trade, securing online transactions has become paramount. Payment fraud attempts have increased exponentially, with cybercriminals targeting everything from individual purchases to large-scale B2B transactions.
Essential Transaction Security Measures:
- SSL/TLS Encryption: Protecting data in transit
- PCI DSS Compliance: Meeting payment card industry standards
- Tokenization: Replacing sensitive data with secure tokens
- Fraud Detection Systems: AI-powered transaction monitoring
Business Continuity: Secure transactions directly impact customer confidence and repeat business. A single security breach can destroy years of customer relationship building and result in significant revenue loss.
4. Preventing Unauthorized Access to Critical Systems
The Perimeter Has Disappeared
Traditional network perimeters no longer exist in today’s cloud-first, remote-work environment. 86% of organizations are adopting zero trust models to address this new reality.
Modern Access Control Strategies:
- Identity and Access Management (IAM): Centralized user authentication
- Privileged Access Management (PAM): Controlling administrative access
- Network Segmentation: Isolating critical systems
- Continuous Authentication: Ongoing verification of user legitimacy
Operational Impact: Unauthorized access can lead to data theft, system manipulation, and operational disruption. The average time to identify and contain a breach involving stolen credentials is 292 days, emphasizing the importance of proactive access controls.
5. Mitigating Cyber Attack Risks and Evolving Threats
The Threat Landscape Evolution
CVE Growth in 2024: A staggering 22,254 CVEs were reported by mid-2024, reflecting a 30% jump compared to 2023. This rapid increase in vulnerabilities requires organizations to maintain robust, adaptive security measures.
Emerging Threat Categories:
- AI-Powered Attacks: Machine learning-enhanced malware
- Supply Chain Attacks: Targeting third-party vendors
- Cloud-Specific Threats: Exploiting misconfigured cloud services
- IoT Vulnerabilities: Securing connected devices
Proactive Defense Strategies:
- Threat Intelligence: Real-time threat monitoring and analysis
- Penetration Testing: Simulated attacks to identify vulnerabilities
- Security Automation: AI-driven threat detection and response
- Incident Response Planning: Structured approaches to breach management
6. Building and Maintaining Customer Trust
Trust as a Competitive Advantage
In an era where data breaches make headlines daily, customers actively choose businesses that demonstrate strong security practices. 94% of businesses scored D or worse for their cybersecurity efforts, with all analyzed companies having experienced a data breach.
Trust-Building Security Measures:
- Transparency: Clear communication about security practices
- Compliance Certifications: Meeting industry-specific requirements
- Regular Security Audits: Third-party validation of security measures
- Customer Education: Helping customers protect themselves
Business Impact: Companies with strong security reputations experience:
- Higher customer retention rates
- Increased willingness to share personal information
- Premium pricing opportunities
- Enhanced brand loyalty and advocacy
7. Ensuring Regulatory Compliance and Avoiding Penalties
The Regulatory Landscape
In 2023, the General Data Protection Regulation (GDPR) imposed record fines exceeding €1.6 billion, demonstrating the severe financial consequences of non-compliance.
Key Regulatory Frameworks:
- GDPR: European Union data protection regulation
- CCPA: California Consumer Privacy Act
- HIPAA: Healthcare data protection requirements
- PCI DSS: Payment card industry security standards
- SOX: Sarbanes-Oxley financial reporting requirements
Compliance Benefits Beyond Avoiding Penalties:
- Structured Security Approach: Regulations provide security framework
- Customer Confidence: Compliance demonstrates commitment to protection
- Competitive Advantage: Meeting higher standards than competitors
- Global Market Access: Enabling international business operations
8. Protecting Intellectual Property and Trade Secrets
The Innovation Imperative
For businesses in competitive industries, intellectual property often represents the most valuable asset. Cyber attacks targeting IP can result in devastating competitive disadvantages and financial losses.
IP Protection Strategies:
- Data Classification: Identifying and categorizing sensitive information
- Access Controls: Limiting IP access to authorized personnel
- Digital Rights Management: Controlling document access and usage
- Insider Threat Detection: Monitoring for internal security risks
Industry-Specific Concerns:
- Technology Companies: Source code and development methodologies
- Healthcare: Research data and clinical trial information
- Financial Services: Trading algorithms and customer analytics
- Manufacturing: Product designs and process innovations
9. Maintaining Business Continuity and Operational Resilience
The Cost of Downtime
Ransomware attacks will strike every 2 seconds by 2031, making business continuity planning essential for organizational survival.
Resilience Framework Components:
- Backup and Recovery: Regular data backups and tested restoration procedures
- Disaster Recovery Planning: Comprehensive incident response protocols
- Business Impact Analysis: Understanding critical processes and dependencies
- Crisis Communication: Maintaining stakeholder confidence during incidents
Operational Benefits:
- Reduced Downtime: Faster recovery from security incidents
- Maintained Productivity: Continued operations during attacks
- Customer Satisfaction: Consistent service delivery
- Financial Stability: Minimized revenue loss from disruptions
10. Protecting National Security and Critical Infrastructure
The Broader Security Ecosystem
Cyber security extends beyond individual organizations to encompass national security and critical infrastructure protection. Cyber-enabled fraud ranks as the second-highest organizational cyber risk for 2025 ttp cybersecurity, with implications for entire economic systems.
Critical Infrastructure Sectors:
- Energy: Power grids and renewable energy systems
- Transportation: Air traffic control and logistics networks
- Healthcare: Hospital systems and medical devices
- Financial Services: Banking networks and payment systems
- Government: Essential services and citizen data
Collective Security Responsibility:
- Information Sharing: Collaborating on threat intelligence
- Public-Private Partnerships: Coordinating security efforts
- Standard Setting: Establishing industry-wide security baselines
- Workforce Development: Training cybersecurity professionals
Implementing Effective Cyber Security: A Strategic Approach
Assessment and Planning
Before implementing security measures, organizations must:
- Conduct Security Audits: Identify current vulnerabilities and risks
- Assess Business Impact: Understand potential consequences of different threats
- Develop Security Policies: Create comprehensive security frameworks
- Establish Budgets: Allocate appropriate resources for security initiatives
Technology Implementation
Core Security Technologies:
- Endpoint Protection: Securing individual devices and workstations
- Network Security: Firewalls, intrusion detection, and monitoring
- Data Encryption: Protecting data at rest and in transit
- Identity Management: Controlling user access and authentication
Advanced Security Solutions:
- Security Information and Event Management (SIEM): Centralized threat monitoring, log archiving, and audit-ready reporting.
- Extended Detection and Response (XDR): Integrated security analytics
- Cloud Access Security Brokers (CASB): Cloud service protection
- Deception Technology: Detecting advanced threats through decoys
Human Factor Considerations
95% of cybersecurity breaches are due to human error, making employee training crucial:
Training Program Components:
- Security Awareness: Understanding common threats and risks
- Phishing Recognition: Identifying suspicious emails and communications
- Password Management: Creating and maintaining strong passwords
- Incident Reporting: Proper procedures for reporting security concerns
Cultural Integration:
- Leadership Commitment: Executive support for security initiatives
- Clear Policies: Understandable security guidelines and procedures
- Regular Updates: Ongoing education about emerging threats
- Positive Reinforcement: Recognizing good security practices
Savvycom’s Comprehensive Cyber Security Solutions
At Savvycom, recognized among the top cybersecurity consulting companies in 2025, we understand that effective cyber security requires more than just technology—it demands strategic thinking, comprehensive planning, and expert implementation. With over 15 years of experience in the technology sector, we’ve established ourselves as a leading cybersecurity consulting provider, helping businesses across fintech, healthcare, and retail sectors build robust security frameworks, with particular expertise in fintech security compliance and risk management that protect against today’s evolving threats.
Our Professional Cybersecurity Services Include:
| Service | Description | Key Benefits |
|---|---|---|
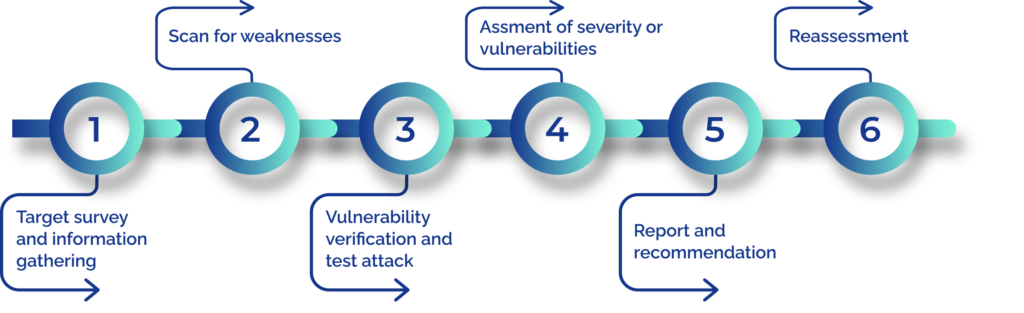
| 🔍 Penetration Testing & Vulnerability Assessment | Thorough security assessments to identify potential vulnerabilities in your systems. We specialize in discovering system cyber security defects and detecting weaknesses missed by other testing methods. | 6-Stage Process |
| ⚔️ Red Team Operations | Real-world cyber attack simulations to assess your organization’s readiness against sophisticated threats. Evaluates effectiveness of security technology, people, and processes. | Threat Simulation |
| 🛡️ Security Operation Center (SOC) | 24/7 monitoring and analysis of your security infrastructure. Dedicated SOC managers, compliance auditors, incident responders, analysts, and threat hunters. | 24/7 Monitoring |
| 🚨 Incident Response & Digital Forensics | Immediate response and thorough digital forensic analysis when security incidents occur. Streamlines threat response while preserving evidence and minimizing business disruption. | Rapid Response |
| 📚 Training & Security Awareness | Comprehensive cybersecurity training programs to educate your workforce about the latest threats and best practices. From basic awareness to advanced threat recognition. | Employee Education |
| ☁️ Managed Security Services | Tailored managed services including infrastructure management, cloud security, IT service management, and continuous monitoring. End-to-end security solutions that scale with your business. | Scalable Solutions |
💡 Why Choose Savvycom? Our comprehensive approach combines technical expertise with strategic business understanding, delivering cost-effective enterprise-grade security solutions.
What Sets Savvycom Apart:
- Proven Track Record: With 200+ satisfied clients and 500+ successful projects, we’ve demonstrated consistent excellence in cybersecurity implementation
- Industry Expertise: Specialized experience in fintech, healthcare, and retail sectors with deep understanding of industry-specific compliance requirements
- Cost-Effective Solutions: Our Vietnam-based operations provide enterprise-grade security services at competitive rates compared to US and European markets, while maintaining standards comparable to cybersecurity in Singapore and other leading technology hubs
- Comprehensive Approach: We combine technical expertise with strategic business understanding to deliver holistic security solutions
- Continuous Innovation: Our team stays ahead of emerging threats through ongoing research and development in cybersecurity technologies
Savvycom’s cybersecurity services stand out due to our comprehensive approach, industry certifications, and proven track record in handling critical vulnerabilities including CVEs and zero-day threats. Our team of seasoned experts provides tailored solutions that ensure robust protection and peace of mind for businesses operating in today’s digital landscape. Our managed SOC services provide 24/7 monitoring and analysis of your security infrastructure, offering specialized security expertise that distinguishes us in the msp vs mssp landscape.
Ready to strengthen your cyber security posture? Contact our experts to discover how we can protect your business from evolving cyber threats.
Ready to Strengthen Your Cyber Security Posture?
At Savvycom, we understand that effective cyber security requires more than just technology—it demands strategic thinking, comprehensive planning, and expert implementation. Our cybersecurity consulting services help businesses across fintech, healthcare, and retail sectors build robust security frameworks that protect against today’s threats while preparing for tomorrow’s challenges.
Contact our cybersecurity experts today to discover how we can help your organization implement comprehensive security measures that protect your data, ensure compliance, and maintain customer trust in an increasingly digital world.
With 15+ years of experience and a proven track record of successful security implementations, Savvycom is your trusted partner for building resilient, secure digital infrastructure that supports business growth and success.
What is the main advantage of cyber security?
The main advantage of cyber security is risk mitigation and business protection. It safeguards valuable assets including customer data, intellectual property, and financial information while ensuring regulatory compliance. Strong cybersecurity measures also build customer trust, enable secure digital transactions, and provide competitive advantages in the marketplace.
Is cybersecurity becoming more important?
Yes, cybersecurity is becoming increasingly critical. CVE vulnerabilities increased by 30% in 2024 with 22,254 reported cases, and 97% of companies report GenAI security issues. As digital transformation accelerates and cyber threats evolve with AI-powered attacks, organizations face exponentially higher risks, making robust cybersecurity essential for business survival.
How does cybersecurity affect us?
Cybersecurity affects us by protecting personal privacy, financial security, and digital infrastructure. It safeguards online transactions, prevents identity theft, ensures healthcare data protection, and maintains critical services like power grids and banking systems. Without proper cybersecurity, individuals and organizations face data breaches, financial fraud, and operational disruptions.
How many cyber attacks a day?
There is a cyber attack every 39 seconds globally, with ransomware attacks projected to strike every 2 seconds by 2031. Organizations experience an average of 3-4 cyberattacks per year, with small businesses being particularly vulnerable. The frequency continues to increase as cybercriminals develop more sophisticated attack methods and AI-powered tools.


