TTP Cybersecurity: A Deep Dive into Modern Threats and Defense Mechanisms
In the digital age, cyber threats have grown in both frequency and complexity, necessitating an advanced understanding of how adversaries operate. The concept of TTP cybersecurity, which stands for Tactics, Techniques, and Procedures, provides a crucial lens through which to view and defend against these evolving threats. By studying the methods that attackers use to infiltrate systems, cyber threat management becomes more proactive and effective. This article will explore the layers of TTP cybersecurity, why it is essential for both individuals and large enterprises, and how top cybersecurity companies are utilizing TTP-based defense strategies to stay ahead of cybercriminals. A software development company can integrate TTP-focused solutions into its processes to enhance overall security. We will dive into technical details, real-world case studies, and explore how this approach can protect critical infrastructure.
1. What is TTP in Cybersecurity?
According to a 2023 report by IBM, 67% of security professionals identified an increase in the sophistication of cyberattacks, many of which rely on TTP strategies, as attackers continuously adapt their methods to evade detection. A 2023 survey by the SANS Institute revealed that 58% of organizations actively use TTP-focused threat intelligence to improve their cybersecurity posture, with an increasing reliance on mapping to frameworks like MITRE ATT&CK.
At its core, TTP cybersecurity focuses on understanding and categorizing the Tactics, Techniques, and Procedures used by cyber adversaries. By breaking down these components, defenders can map out potential attack scenarios and develop comprehensive defense strategies.
- Tactics refer to the overarching strategies employed by attackers. This could be something as broad as gaining unauthorized access to a system or maintaining persistence within a network.
- Techniques are the specific methods attackers use to achieve their tactical goals. For example, phishing is a technique used to gain initial access by tricking users into revealing credentials.
- Procedures refer to the step-by-step actions or workflows that attackers follow to execute their techniques. These can include customized malware scripts or exploitation tools.
Understanding TTPs goes beyond merely detecting known malware signatures or suspicious network behavior. It involves anticipating what attackers are trying to accomplish and how they might go about achieving it. One of the most significant frameworks for categorizing TTPs is MITRE ATT&CK, a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations.
The Role of TTPs in Proactive Defense
While traditional cybersecurity measures focus on reactive approaches such as detecting malware based on signatures, TTP cybersecurity shifts the focus to a more proactive defense. By analyzing TTPs, organizations can predict attacker behavior and prevent breaches before they escalate.
To draw an analogy, imagine defending a castle. While setting traps (like firewalls) can deter intruders, studying how enemies move (TTPs) allows you to anticipate their actions, strengthen weak points, and block routes they are likely to take. This analogy perfectly illustrates how TTP cybersecurity helps defend digital landscapes by predicting adversary behavior rather than just reacting to attacks.
2. The Role of TTPs in Cybersecurity: A Multi-layered Approach
When integrated into a larger cyber threat management framework, TTPs allow for a much more comprehensive and nuanced understanding of the attack lifecycle. Here’s how TTP cybersecurity contributes to various facets of security:
2.1 TTPs in Threat Hunting
Threat hunting, a proactive search for threats that have infiltrated a system, relies heavily on TTPs. By analyzing patterns of activity associated with specific adversaries, security analysts can identify abnormal behavior that may otherwise go undetected by automated systems. In many cases, this means searching for subtle signs like command-line activities, unauthorized software installations, or lateral movement within a network.

Image source: Logpoint
For example, an attacker might employ a known tactic like spear-phishing to gain initial access, use a technique like credential dumping to steal passwords, and then proceed to lateral movement through the network by abusing valid credentials. Knowing the TTPs associated with a particular group or campaign allows security teams to detect this behavior at an early stage, significantly reducing response time.
2.2 Incident Response and Recovery
Incident response teams also benefit from TTP intelligence. When a breach occurs, identifying the Tactics, Techniques, and Procedures used can help determine the scope of the incident and how to contain it. This allows for more effective remediation. By focusing on the attacker’s TTPs, incident responders can trace back how the attack occurred, prevent further escalation, and implement safeguards against similar tactics in the future. In fact, organizations using TTP-based detection reduced the time to identify and contain breaches by 27% on average, as reported in a 2022 Ponemon Institute study on data breach costs.
2.3 Penetration Testing and Red Teaming
Penetration testing and red teaming exercises use TTP cybersecurity principles to simulate real-world cyberattacks. Red teamers specifically emulate adversary behavior, using tactics and techniques that mirror those used in known attack campaigns. This allows organizations to test their defenses under realistic conditions and prepare for potential breaches.
For example, during a red teaming exercise, testers may employ techniques like credential stuffing (a common attacker technique) to see if an organization has adequate protections in place. The more the TTPs mirror real-world attacks, the better prepared the organization will be.
3. Common Tactics Used by Cyber Adversaries
TTPs cover a broad range of activities, but some of the most commonly observed tactics in modern cybersecurity incidents include:
- Initial Access: Gaining unauthorized entry into a network is often the first step in an attack. This can happen through phishing, exploiting vulnerabilities in internet-facing services, or brute-forcing weak credentials.
- Execution: Once access is obtained, attackers execute malicious code or scripts to carry out the attack. This may involve running ransomware or remote access tools.
- Persistence: Attackers aim to maintain long-term access by using techniques like installing backdoors or manipulating authentication mechanisms to avoid detection.
- Privilege Escalation: After gaining a foothold, adversaries often seek to increase their privileges within the system, allowing them greater control and access to sensitive data.
- Lateral Movement: Attackers move within the network to find valuable targets, often using compromised credentials to navigate between systems.
- Exfiltration: The goal of many cyberattacks is to steal data, which can be done using various techniques such as compressing and encrypting files before sending them out of the network.
Real-World Case Study: SolarWinds Attack
The 2020 SolarWinds cyberattack is one of the most notorious examples of TTP cybersecurity in action. The attackers inserted malicious code into SolarWinds’ Orion software, which was used by thousands of organizations, including Fortune 500 companies and U.S. government agencies. Once the compromised update was installed, attackers gained initial access and used privilege escalation and lateral movement techniques to spread within networks. By studying the TTPs used in SolarWinds, cybersecurity professionals were able to better understand how to protect against supply chain attacks in the future.
This breach underscores the importance of TTP cybersecurity in preventing, detecting, and mitigating advanced persistent threats (APTs). By mapping the attack’s TTPs to the MITRE ATT&CK framework, defenders could pinpoint gaps in their security infrastructure and develop more robust defense strategies.
Looking For a Trusted Tech Partner?
We’ll help you decide on next steps, explain how the development process is organized, and provide you with a free project estimate.
4. Techniques: Unpacking the Tools of Cyber Adversaries
Techniques used by attackers are varied and can be tailored to exploit specific vulnerabilities in a target’s system. Here are a few common ones:
- Credential Dumping: Attackers extract credentials from system memory, hashes, or other sources to gain unauthorized access. These credentials can then be used to impersonate legitimate users within the network.
- Spear Phishing: Targeted phishing attacks, often customized with specific personal or organizational information, trick users into revealing sensitive data.
- Command and Control (C2): Attackers maintain communication with compromised systems through remote servers, allowing them to issue commands and retrieve data.

Image source: ICSS
Case Study: Colonial Pipeline Ransomware Attack
In 2021, the Colonial Pipeline ransomware attack leveraged several key TTPs. The attackers gained initial access by exploiting weak credentials through a password reuse attack. They then deployed ransomware to lock down critical infrastructure. By understanding the attackers’ TTPs, security teams were able to respond more effectively, isolating affected systems and preventing further damage.
5. Procedures: Execution of Cyber Attacks
Procedures involve the specific tools and methodologies attackers use to execute their techniques. These can vary widely depending on the skill level of the adversary and the nature of the attack. For example, a ransomware group might use an off-the-shelf malware toolkit, while a nation-state actor may develop bespoke malware designed to avoid detection.
An example of advanced procedures can be seen in a targeted attack on a large energy provider. Attackers first gained initial access through a phishing campaign targeting high-level employees. They used customized malware to avoid antivirus detection and employed C2 channels that mimicked legitimate web traffic. This sophisticated procedure allowed the attackers to remain undetected for months while they exfiltrated sensitive data.
6. Defensive Strategies for Mitigating TTPs
Defending against TTPs requires a multi-layered approach that integrates cyber threat management, continuous monitoring, and TTP intelligence.
Penetration Testing and Red Teaming
One of the most effective ways to mitigate TTP-based threats is through penetration testing and red teaming exercises. By simulating real-world attacks using known TTPs, organizations can uncover vulnerabilities and test their defenses under realistic conditions.
Companies like Savvycom, a leading software development company, offer ttp cybersecurity solutions that include penetration testing and red teaming. These services are crucial for businesses that want to proactively protect their IT infrastructure.
Threat Intelligence Platforms
To prevent cyberattacks before they happen, top cybersecurity companies use threat intelligence platforms (TIPs) to aggregate data on known attack techniques. These platforms analyze real-world attacks to create threat profiles that include TTPs from observed cyber incidents. This information helps cybersecurity professionals detect attack patterns before they escalate into a full-blown breach.
One leading example is FireEye’s Threat Intelligence Platform, which gathers data from their investigations and combines it with TTP intelligence to offer preemptive alerts to organizations. By applying this intelligence, companies can fine-tune their defenses and gain early warnings of imminent attacks based on specific TTPs.
Savvycom, a renowned software development company, also offers cybersecurity services like ttp cybersecurity solutions to enterprises looking to fortify their networks against these threats.
Behavioral Analytics and Machine Learning
Many organizations are leveraging machine learning to identify TTPs by studying user and system behavior. Behavioral analytics can detect anomalies, such as unauthorized access attempts or unusual data transfers, that align with known adversary tactics. These systems create baseline models of normal behavior and flag deviations that resemble TTP-based activities.
Machine learning algorithms can classify techniques like brute-force attempts, lateral movement, or data exfiltration by looking at network activity patterns and automatically generate alerts. These adaptive systems are particularly effective in spotting zero-day attacks—exploits that use previously unknown vulnerabilities—by recognizing deviations from typical behavior.
Case Study: Microsoft Exchange Server Attack
In 2021, hackers exploited vulnerabilities in Microsoft Exchange Server to gain access to email accounts and install backdoors. By employing TTP intelligence, the cybersecurity team at Microsoft identified patterns of lateral movement and privilege escalation consistent with advanced persistent threat (APT) groups. This allowed them to issue immediate patches and advisories for affected organizations, stopping further attacks.
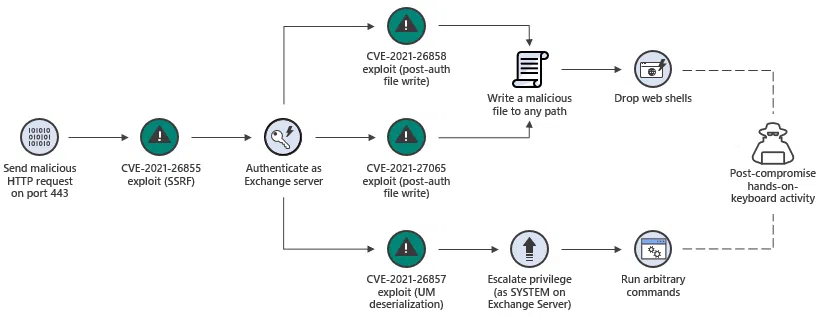
Image source: Microsoft
7. Challenges in Implementing TTP Cybersecurity
Despite its strengths, implementing a TTP cybersecurity framework comes with challenges:
- Constant Evolution: Adversaries are continually evolving their TTPs, making it difficult for defense systems to keep up. What works today may be obsolete tomorrow.
- Resource Intensive: Studying TTPs requires significant resources, both in terms of technology and skilled personnel. Smaller organizations might struggle to implement TTP-based defenses without help from third-party providers.
- Data Overload: Handling the sheer volume of data associated with TTP intelligence can overwhelm security teams. Threat intelligence feeds can generate false positives, and distinguishing between legitimate threats and harmless anomalies is an ongoing challenge.
Despite these obstacles, investing in TTP cybersecurity is essential for organizations that want to maintain an effective defense against modern cyber threats. The benefits of understanding and anticipating adversary behavior far outweigh the challenges, particularly in industries like finance and healthcare, where data breaches can have catastrophic consequences.
8. Future Outlook: The Role of Automation and AI in TTP Cybersecurity
As cyber threats continue to evolve, so too must our defenses. One key trend shaping the future of TTP cybersecurity is the increasing role of automation and AI in threat detection and mitigation.
Automated systems, powered by artificial intelligence (AI), can process vast amounts of data and correlate behaviors across multiple attack vectors faster than human analysts. Machine learning algorithms continuously refine their understanding of TTPs by analyzing historical attack data, improving their ability to detect future threats.
Moreover, AI-driven automation in threat response can reduce the time from detection to remediation. For example, AI tools can automatically isolate infected systems, block suspicious IP addresses, or even patch vulnerabilities in real-time, allowing security teams to focus on higher-level strategic decision-making.
Emerging Technologies and TTP-based Defense
Another emerging trend is the use of zero-trust security in combination with TTP intelligence. Zero-trust models operate on the assumption that no user or device should be trusted by default. Instead, they continuously authenticate and authorize access based on real-time analysis of TTPs and behavior patterns. By integrating TTP-based threat intelligence with a zero-trust model, organizations can drastically reduce the risk of insider threats and lateral movement within their networks.
Leading software development companies like Savvycom are already incorporating these trends into their cybersecurity offerings, providing ttp cybersecurity solutions that leverage AI and machine learning for advanced threat detection and response.
The Imperative of TTP Cybersecurity
In today’s digital landscape, defending against cyberattacks requires a deeper understanding of how attackers operate. TTP cybersecurity gives organizations a strategic advantage by enabling them to anticipate and mitigate threats before they cause irreparable harm.
From identifying attacker behavior during threat hunting to refining defenses through penetration testing, TTPs are integral to modern cyber threat management. By studying adversarial Tactics, Techniques, and Procedures, organizations can proactively defend their assets and reduce the likelihood of costly breaches.
As the cybersecurity landscape continues to evolve, companies must embrace the principles of TTP cybersecurity to stay ahead of attackers. Through automation, AI, and zero-trust models, the future of TTP-based defense will be more dynamic and adaptive than ever before.
Savvycom offers a wide range of cyber security outsourcing services, including penetration testing, red teaming, and digital forensics. With the help of Savvycom, organizations can enhance their defenses by utilizing the latest advancements in TTP intelligence and cybersecurity solutions. Contact Savvycom today to learn more about how ttp cybersecurity can fortify your organization’s defenses against evolving cyber threats.
Tech Consulting, End-to-End Product Development, Cloud & DevOps Service! Since 2009, Savvycom has been harnessing digital technologies for the benefit of businesses, mid and large enterprises, and startups across the variety of industries. We can help you to build high-quality software solutions and products as well as deliver a wide range of related professional services.
Savvycom is right where you need. Contact us now for further consultation:
- Phone: +84 24 3202 9222
- Hotline: +1 408 663 8600 (US); +612 8006 1349 (AUS); +84 32 675 2886 (VN)
- Email: [email protected]


