Zero Trust Architecture: A New Frontier in Cybersecurity in Singapore
In recent years, Singapore has rapidly emerged as a global technology hub, embracing artificial intelligence (AI) to fuel its ambition of becoming the world’s first fully realized Smart Nation. AI technology, integrated into everything from healthcare to urban planning, is central to Singapore’s Smart Nation strategy. As the city-state leverages AI to streamline its public services and optimize resource allocation, businesses also recognize the significant advantages of this transformation. For tech companies, including a top software development company, Singapore’s dedication to innovation provides fertile ground for advancing AI capabilities.
With the rapid proliferation of cyberattacks and rising data privacy concerns, businesses in the region are relying on AI-powered systems to enhance security protocols. Many firms, including those that partner with software outsourcing Vietnam, are developing smarter, more secure systems that can respond to threats in real time.
In this article, we will examine how AI is helping Singapore achieve its Smart Nation ambitions, explore related case studies, and discuss how Savvycom contribute to AI-powered digital transformation solutions. The collaboration between AI innovators and businesses is setting the stage for Singapore to continue leading the charge in global tech innovation.
Source: EDB Singapore
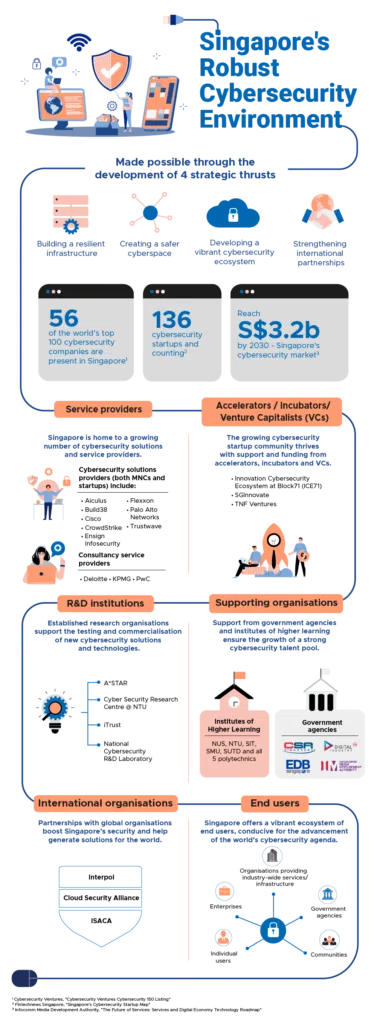
The Growing Threats of Cybersecurity in Singapore
Singapore, recognized as one of the most digitalized nations in the world, is facing a growing wave of cyberattacks. The adoption of cloud technology, IoT devices, and AI solutions has expanded the attack surface, making businesses more vulnerable to sophisticated cyber threats. In 2022 alone, Singapore saw a significant rise in cyber incidents, with ransomware attacks and phishing being the most common forms of attack. According to the Cyber Security Agency of Singapore (CSA), there was a 154% increase in ransomware incidents from the previous year, and phishing attacks nearly doubled, targeting both individuals and businesses.
In particular, the financial and healthcare sectors have become key targets for hackers due to the sensitive nature of the data they hold. Singapore’s healthcare sector experienced a data breach that affected 1.5 million patients in 2018, including the personal data of the Prime Minister. This high-profile incident highlighted the urgent need for enhanced cybersecurity frameworks. The country’s rapidly expanding smart infrastructure, along with its reliance on AI and data, presents both an opportunity and a challenge.
Why Zero Trust Architecture Is the Future of Cybersecurity in Singapore
In response to escalating cyber threats, organizations can no longer rely on traditional perimeter-based security models. These models are outdated in the context of cloud-first, mobile workforces, and IoT environments. Here, Zero Trust Architecture becomes pivotal. The principle behind Zero Trust is simple: “Never trust, always verify.” This model assumes that no entity—whether inside or outside an organization’s network—should be trusted by default. Every user and device attempting to access the system must be authenticated and authorized.
Singapore’s government has recognized the importance of ZTA. As part of the Singapore Cybersecurity Strategy 2021, there is a strong focus on strengthening the country’s resilience against cyberattacks. The strategy emphasizes proactive cyber defense, including implementing Zero Trust principles across public and private sectors to reduce risks.
Key Elements of Zero Trust Architecture
-
Identity and Access Management (IAM): Only authorized users can access sensitive data, with multi-factor authentication (MFA) serving as a critical layer.
-
Micro-Segmentation: By dividing the network into smaller segments, each access request is restricted to only the resources the user or device needs, reducing the risk of lateral movement.
-
Continuous Monitoring: With Zero Trust, the security framework continuously monitors traffic and behavior to detect anomalies that could indicate a breach.
The Role of AI and Automation in Cybersecurity in Singapore
Artificial Intelligence (AI) plays a crucial role in Zero Trust Architecture, especially in automating threat detection and response. In Singapore, AI-driven cybersecurity solutions are becoming more prevalent, allowing real-time analysis of vast amounts of data to identify unusual behavior. AI reduces the burden on cybersecurity teams by filtering out false positives and providing actionable insights.
According to a report by Vorecol, AI-driven cybersecurity solutions could mitigate risks faster than human-managed systems by over 50%. For cybersecurity in Singapore, which is constantly under threat from state-sponsored attacks and highly motivated criminal organizations, leveraging AI in Zero Trust frameworks is a critical advantage.
Get in touch with Savvycom for a free consultation. We’ll help you decide on next steps, explain how the development process is organized, and provide you with a free project estimate.
Critical Advantages of Zero Trust for Singapore
Cybersecurity plays a pivotal role in supporting Singapore’s key sectors such as finance, healthcare, and government operations, the Zero Trust approach offers not just protection but also enhances operational efficiency, compliance, and resilience.
-
Minimized Attack Surface
Singapore’s reliance on digital infrastructure exposes it to an increasing number of cyber threats, from ransomware to state-sponsored espionage. One of the key benefits of Zero Trust is its ability to minimize the attack surface by enforcing strict access controls. Traditional perimeter-based security models leave gaps, especially when facing external threats. ZTA, however, assumes no entity—whether internal or external—is trustworthy by default. This approach ensures that only verified users and devices can access specific parts of the network, thereby reducing the potential points of entry for cyber attackers. -
Enhanced Data Security in Critical Sectors
Data breaches can have catastrophic consequences, especially in critical sectors like healthcare and finance. Singapore, with its strong emphasis on data protection, stands to benefit from Zero Trust’s continuous authentication and encryption protocols. ZTA ensures that even if one section of the network is compromised, sensitive data remains secure, significantly limiting the potential damage. In sectors where confidentiality is non-negotiable, Zero Trust Architecture can act as a critical safeguard. -
Improved Compliance with Data Protection Regulations
With data protection laws such as Singapore’s Personal Data Protection Act (PDPA) becoming stricter, compliance is a major concern for organizations. Zero Trust, by ensuring secure, encrypted access to sensitive data and monitoring interactions across the network, helps businesses adhere to these regulations. Moreover, by employing granular access controls and encryption, organizations can demonstrate compliance more effectively, thereby avoiding hefty penalties and reputational damage. -
Faster Detection and Mitigation of Cyber Threats
One of the primary advantages of Zero Trust is its ability to rapidly detect and respond to suspicious activities within the network. Traditional models may fail to catch breaches early, but with continuous real-time monitoring, ZTA enables rapid detection of anomalies. This leads to swift incident responses and minimizes the potential fallout from an attack. In a city-state like Singapore, where cybersecurity incidents can have nationwide implications, this rapid response capability is invaluable. -
Boosting Agility and Innovation
Adopting Zero Trust does not only fortify security but also enhances business agility. With digital transformation initiatives such as Smart Nation being a priority, businesses in Singapore need cybersecurity solutions that can scale with growth while ensuring uncompromised security. Zero Trust supports secure remote work environments, cloud adoption, and the use of Software-as-a-Service (SaaS) applications, which are critical for businesses that want to innovate without compromising security.

ZTA in cybersecurity in Singapore
Case Study: Zero Trust in Cybersecurity in Singapore
The move towards Zero Trust Architecture in cybersecurity in Singapore demonstrates a proactive approach to addressing the evolving cyber threat landscape. By implementing stringent access controls, continuous monitoring, and identity verification, organizations across various sectors are not only enhancing their security postures but also fostering trust among stakeholders. As the complexity of cyber threats increases, Singapore’s commitment to Zero Trust will be critical in safeguarding its digital landscape.
1. Singapore’s Government Cyber Security Agency (CSA)
The Cyber Security Agency of Singapore (CSA) has been at the forefront of implementing Zero Trust principles across government agencies. In 2020, the CSA launched its “Cybersecurity Strategy 2020”, which emphasizes adopting a Zero Trust Architecture to protect critical information infrastructure. This strategy aims to reduce the attack surface by verifying every device and user attempting to access the network, rather than relying solely on perimeter defenses.
Outcome: This initiative has significantly enhanced the resilience of Singapore’s public sector against cyber threats. By implementing Zero Trust, agencies can ensure that only authenticated users and devices can access sensitive data, mitigating risks of data breaches.
2. Financial Sector Transformation
In the financial services sector, several banks in Singapore, including DBS Bank and UOB, have begun adopting Zero Trust models to safeguard customer data and financial transactions. For example, DBS Bank has implemented strict identity verification processes and continuous monitoring of user activity within its systems. This approach not only protects sensitive information but also complies with the Monetary Authority of Singapore’s (MAS) regulations on cybersecurity.
Outcome: By integrating Zero Trust principles, these banks reported a significant decrease in unauthorized access attempts, enhancing overall customer trust and satisfaction.
3. Enterprise Adoption in Tech Firms
Local tech firms in Singapore have also embraced Zero Trust Architecture as part of their cybersecurity strategy. A notable example is Grab, Southeast Asia’s leading super app. Grab has adopted a Zero Trust model to ensure that every access request, whether internal or external, is treated with skepticism. They use advanced analytics and machine learning to assess risks in real-time, ensuring that only legitimate users can access sensitive data.
Outcome: This has resulted in a more agile response to potential threats, allowing Grab to maintain its reputation as a secure platform for millions of users.
4. Healthcare Sector Implementation
The Singapore General Hospital (SGH) has incorporated Zero Trust principles to protect patient data against increasing cyber threats. By utilizing identity and access management solutions, SGH ensures that only authorized personnel can access patient records and other sensitive information.
Outcome: The adoption of this architecture has led to improved patient data security, reducing incidents of data breaches and ensuring compliance with healthcare regulations.
How Singaporean Businesses Can Implement Zero Trust
Implementing Zero Trust requires a clear strategy and investment in advanced security technologies. To begin with, organizations must evaluate their current infrastructure and identify gaps in security. Partnering with experienced software development companies like Savvycom can simplify the transition by providing customized Zero Trust solutions tailored to your organization’s needs.
Savvycom has positioned itself as a leading provider of cybersecurity solutions, helping businesses in Singapore and Southeast Asia adopt Zero Trust frameworks. With its proven track record in AI-powered cybersecurity solutions, cloud security, and software development, Savvycom delivers tailored, scalable strategies that enhance the security posture of organizations. Savvycom’s Zero Trust-based security solutions ensure continuous monitoring, data protection, and risk mitigation, keeping businesses secure in an ever-evolving threat landscape.
Whether it’s multi-factor authentication (MFA), cloud access security brokers (CASB), or AI-driven threat detection systems, Savvycom’s cybersecurity solutions help businesses stay ahead of cyber risks while ensuring compliance with local regulations.
FAQs
Why is Zero Trust critical for cybersecurity in Singapore?
Given Singapore’s status as a global financial hub and its extensive digital infrastructure, the city-state is a prime target for cybercriminals. According to the Cyber Security Agency of Singapore (CSA), the number of cyber incidents has surged in recent years, particularly in critical sectors like government, finance, and healthcare. Implementing a Zero Trust model enhances resilience against sophisticated attacks by ensuring that even trusted users and devices are scrutinized before gaining access to sensitive systems and data. This layered security strategy is vital for maintaining public trust and safeguarding national security .
How can small businesses implement Zero Trust?
Small businesses can adopt Zero Trust principles by implementing several key strategies:
- Multi-Factor Authentication (MFA): This adds an extra layer of security by requiring users to provide multiple forms of identification before accessing systems.
- Micro-Segmentation: This involves dividing the network into smaller, isolated segments to limit the movement of threats within the network.
- Real-Time Monitoring: Continuous monitoring of network traffic can help detect anomalies and potential threats before they escalate.
- Collaborating with a software development company like Savvycom can provide tailored solutions that integrate advanced security measures to fit the specific needs of smaller enterprises .
How does Zero Trust differ from traditional security models?
Traditional security models often rely on a strong perimeter defense, assuming that users inside the network can be trusted. In contrast, Zero Trust operates under the assumption that both internal and external networks are potentially compromised. As such, it requires continuous verification for every access request, regardless of the user's location. This shift in mindset fundamentally changes how organizations approach cybersecurity, focusing more on identity and context rather than mere network location .
Can Zero Trust help with compliance regulations?
Absolutely. Zero Trust Architecture assists organizations in adhering to various regulatory frameworks, such as Singapore’s Personal Data Protection Act (PDPA). By ensuring strict access controls, encrypting sensitive data, and maintaining continuous monitoring, organizations can demonstrate compliance with regulatory requirements. Moreover, this approach allows for more effective data governance and risk management strategies.
To further understand the transformative impact of Zero Trust Architecture (ZTA) on modern cybersecurity, watch this informative video that breaks down the core principles and benefits of ZTA, showcasing how it secures organizations in an evolving threat landscape.
Conclusion: The Future of Cybersecurity in Singapore Lies in Zero Trust
As the cyber threat landscape evolves, cybersecurity in Singapore will increasingly depend on the widespread adoption of Zero Trust Architecture. By assuming no one can be trusted by default, Zero Trust minimizes the risk of insider threats and external attacks, while empowering organizations with continuous protection.
Partnering with cybersecurity experts of Savvycom enables businesses to adopt cutting-edge technologies and advanced security frameworks that meet the demands of today’s digital economy. Investing in Zero Trust today is a commitment to protecting your business’s future in an increasingly connected world. For tailored Zero Trust solutions and comprehensive security strategies, contact Savvycom today to secure your digital infrastructure.


