Web App Security: 2025 Complete Guide
The Increasing Importance of Web App Security in 2025
Web applications are a vital part of most businesses today, whether you’re running an e-commerce platform, a financial service, or a content delivery network. However, as reliance on web applications grows, so do the threats associated with them. The evolution of cybercrime has seen attackers become more sophisticated, and the attack surface for web applications has expanded due to advances in APIs, microservices, and distributed architectures.
In 2025, the cost of data breaches continues to rise, putting immense pressure on businesses to secure their web applications effectively. According to IBM’s 2024 Cost of a Data Breach Report, the average cost of a data breach has reached $4.88 million, up from $4.35 million in 2023. Furthermore, Gartner’s API Security Report highlighted that API vulnerabilities accounted for 33% of web app breaches in 2024, and this number is expected to grow with the increasing adoption of API-driven architectures.

Image source: Abnormal Security
These statistics highlight the critical importance of web app security in today’s digital world. With the growing sophistication of cyberattacks, securing web apps is no longer optional—it’s a business imperative. Companies that fail to invest in security risk data breaches, reputational damage, and financial losses that could prove fatal to their business.
The Fundamentals of Web App Security
At its core, web app security refers to the protective measures and practices that defend web applications against cyber threats. These practices range from securing user authentication and input validation to encryption and real-time threat detection. Below, we explore the essential pillars of securing web apps.
Authentication and Authorization: Ensuring Secure Access
Authentication confirms the identity of a user, while authorization determines the actions that user is allowed to perform within the application. Inadequate authentication and authorization mechanisms are among the most exploited vulnerabilities in web applications.
Google has been a leader in implementing multi-factor authentication (MFA) across its entire platform. Since implementing MFA across Gmail and other Google services, the company reported a 99.9% decrease in successful phishing attacks. This showcases how critical strong authentication is in protecting web applications from unauthorized access. John Wu, Head of Cybersecurity at Cloudflare, notes: “Weak or stolen passwords are responsible for the majority of breaches. Implementing MFA, along with session management practices like timeouts and IP whitelisting, drastically reduces the attack surface.”
Input Validation: Protecting Against Injection Attacks
Web apps often process large amounts of user input, and this input can be manipulated by attackers. Ensuring that data is validated and sanitized before processing is crucial to protecting against attacks like SQL injection and Cross-Site Scripting (XSS).
In 2025, SQL injection remains a prevalent threat. Hackers inject malicious SQL queries into input fields, manipulating the database to reveal sensitive information. According to OWASP, 25% of web apps are still vulnerable to SQL injection, making it a key risk area for developers.
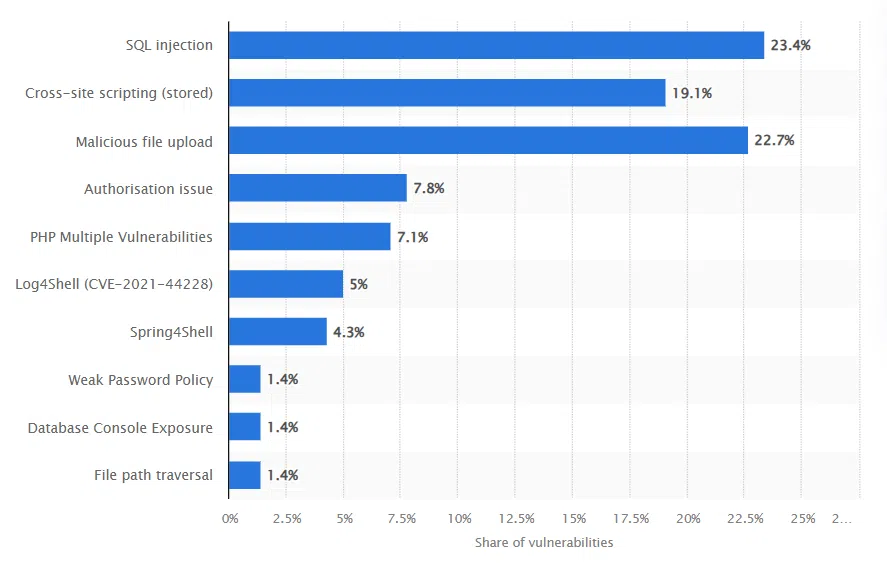
Image source: Statista
Pro Tip:
- Use parameterized queries or prepared statements to prevent SQL injection.
- Implement content security policies (CSPs) to mitigate XSS vulnerabilities.
Looking For a Trusted Tech Partner?
We’ll help you decide on next steps, explain how the development process is organized, and provide you with a free project estimate.
Data Encryption: Securing Data in Transit and at Rest
Encryption ensures that sensitive information, whether in transit between the client and the server or stored in the database, remains confidential and secure. In 2025, encryption is not just recommended—it’s a necessity, especially for industries dealing with financial transactions, personal health information, or intellectual property.
Stripe, one of the world’s leading payment gateways, uses end-to-end encryption (E2EE) to protect credit card information. By employing Advanced Encryption Standards (AES-256) for its data, Stripe has effectively minimized the risk of data breaches. Elizabeth Ramirez, Chief Security Officer at Stripe, emphasizes, “Encryption is the foundation of data security in any modern web application. Beyond TLS/SSL for data in transit, full-disk encryption is essential for sensitive data at rest.”
Session Management: Securing User Sessions
Sessions are created when users interact with a web application, and they store critical information such as login credentials and user-specific data. Session hijacking occurs when attackers take control of an active session, often through vulnerabilities in cookie management.
The Impact of Poor Session Management
In 2025, a major e-commerce platform suffered a significant data breach due to insecure session management. Attackers exploited sessions that did not expire properly, allowing them to access customer accounts long after the original session had ended. The breach cost the company millions in fines and a massive loss of consumer trust.
Session Management Best Practices:
- Use secure cookies (HTTPOnly and Secure flags).
- Implement session timeouts for inactive users.
- Regularly refresh and rotate session tokens.
API Security: Securing the Backbone of Modern Web Apps
As web applications increasingly rely on APIs to exchange data and functionality with other systems, API security has become a focal point. Insecure APIs are a primary attack vector for many cybercriminals.
In 2025, a massive breach occurred at T-Mobile, where attackers exploited vulnerable API endpoints, gaining access to customer account details, including phone numbers and addresses. This breach affected over 40 million users and highlighted the critical need for stringent API security practices.
Expert Advice: David Kennedy, Founder of TrustedSec and former Chief Security Officer at Diebold, recommends, “API security requires end-to-end encryption, proper authentication tokens, and a zero-trust model. Regular audits are essential to identify exposed or poorly secured APIs.”
Common Web App Vulnerabilities: 2025 Overview
These statistics reflect the growing need for robust security practices. With SQL Injection affecting 25% of web applications, attackers exploit poorly validated input fields to manipulate databases, causing data breaches. Cross-Site Scripting (XSS), present in 18% of web apps, allows malicious scripts to be injected into webpages, compromising user interactions. Broken authentication stands out as a major vulnerability in 27% of apps, where attackers exploit weak login mechanisms. Finally, Insecure APIs are the most prevalent, affecting 33% of applications, providing attackers with unauthorized access to backend systems if endpoints aren’t properly secured. Addressing these vulnerabilities requires a proactive approach to ensure web app security in 2025.
Attack vectors in web app security can take many forms, each posing significant threats to the integrity and functionality of applications. One common method involves injecting malicious SQL code into web forms, enabling attackers to manipulate databases and gain unauthorized access to sensitive information. Another frequent tactic is embedding harmful scripts into web pages, which can lead to Cross-Site Scripting (XSS) attacks, allowing the execution of malicious code in users’ browsers. Weak or improperly managed authentication tokens also present a major risk, as they can be exploited to hijack user sessions and gain unauthorized control. Additionally, unsecured API endpoints are increasingly targeted by cybercriminals, as they provide direct access to backend systems and data if not properly secured. Addressing these vulnerabilities is essential for maintaining robust web app security.
Security Testing and Continuous Monitoring
Regular testing of web applications is vital to identifying and patching security vulnerabilities before they can be exploited. Penetration testing and vulnerability scanning are essential tools in this process.
Facebook uses automated security testing tools like Burp Suite and OWASP ZAP to continuously monitor its web applications for vulnerabilities. These tools simulate real-world attacks and provide detailed reports that help engineers secure the platform.
Best Practices for Security Testing:
- Conduct regular penetration tests to uncover hidden vulnerabilities.
- Use static and dynamic application security testing (SAST and DAST) tools for continuous monitoring.
Have a Project Idea in Mind?
Get in touch with Savvycom’s experts for a free consultation. We’ll help you decide on next steps, explain how the development process is organized, and provide you with a free project estimate.
Advanced Security Techniques for 2025
As cybercriminals evolve, so must security practices. In 2025, advanced techniques such as AI-driven threat detection, DevSecOps, and automated patch management are becoming essential for any organization serious about web app security.
AI-Driven Threat Detection
AI and machine learning (ML) are revolutionizing cybersecurity. AI-driven tools can detect anomalies in user behavior, traffic patterns, and application usage, which helps identify potential threats before they materialize into full-blown attacks.
Image source: techmango
AI in Threat Detection at Darktrace Darktrace, a leading AI-based cybersecurity firm, uses machine learning algorithms to detect subtle patterns in data traffic. In 2024, Darktrace’s AI systems successfully neutralized several major cyber threats, saving businesses billions in potential losses.
DevSecOps: Integrating Security in Development
The traditional separation of development, operations, and security is quickly becoming obsolete. DevSecOps integrates security at every phase of the development lifecycle, from coding to deployment and beyond. Julia Hunter, a DevSecOps Specialist at GitHub, says, “Security must be baked into the development process, not added as an afterthought. DevSecOps helps automate security checks, reducing the burden on developers while ensuring that security is never compromised.”
Supply Chain Security: Addressing Third-Party Risks
As businesses rely more on third-party components and libraries in their web applications, supply chain attacks have become a growing concern. Attackers can inject malicious code into third-party software, which is then distributed to all users of that software.
The SolarWinds attack in 2020 was one of the most damaging supply chain attacks in history, but its impact is still felt today. In 2025, businesses are more cautious about third-party software, conducting rigorous code audits and monitoring for vulnerabilities.
Best Practices for Supply Chain Security:
- Use software composition analysis (SCA) tools to track the use of third-party libraries and identify vulnerabilities.
- Conduct regular audits of vendor code.

Image source: Anant Upadhyay
Savvycom’s Role in Web App Security
At Savvycom, we recognize that web app security is no longer just about patching vulnerabilities; it’s about creating a resilient, future-proof security architecture that evolves with emerging threats. As a forward-thinking software development company, we understand that today’s digital environment demands a holistic, adaptive approach to security—one that aligns with business goals while protecting critical assets.
Comprehensive, End-to-End Security Solutions
Savvycom’s expertise in web application development extends far beyond building functional applications. From the very inception of a project, our teams work collaboratively with clients to embed security-first principles into the entire development lifecycle—a practice known as Secure Development Life Cycle (SDLC). This ensures that your web applications are built with robust security features at their core, rather than treating security as an afterthought.
Specialization Across Key Industries: Tailored Solutions
Savvycom’s unique strength lies in its ability to customize security strategies to fit the specific needs of industries with heightened security requirements, such as healthcare, finance, and education. Each industry faces its own set of challenges—ranging from compliance with healthcare regulations like HIPAA to financial data integrity under PCI-DSS standards—and our security experts are adept at creating solutions that meet both regulatory and business needs.
For example, in healthcare, where patient confidentiality and data integrity are paramount, we implement end-to-end encryption across all communication channels and ensure that data-at-rest is fully protected. Our approach to finance focuses heavily on multi-factor authentication (MFA) and fraud detection systems, crucial for maintaining the trust of financial clients and regulatory bodies alike.

Proactive Threat Intelligence and Real-Time Monitoring
As cyberattacks become more sophisticated, the ability to anticipate and respond to threats in real-time is critical. Savvycom’s security framework goes beyond static defenses and embraces proactive threat intelligence. Using AI-powered anomaly detection and real-time monitoring systems, we provide an added layer of security that helps detect and mitigate suspicious activity before it escalates into a breach.
We leverage automated tools to continuously scan for vulnerabilities, but our approach also incorporates manual reviews by expert cybersecurity teams who understand the nuances of specific attack vectors. This hybrid approach ensures that no potential threat is overlooked and that your web applications remain secure in an ever-evolving threat landscape.
DevSecOps Integration: Merging Development and Security
Security isn’t just the responsibility of cybersecurity teams—it’s baked into every aspect of the DevOps pipeline at Savvycom through DevSecOps integration. By aligning development, operations, and security teams, we automate security practices like code scanning and vulnerability checks at every stage of the development process. This approach reduces human error and accelerates the delivery of secure, scalable web applications, empowering businesses to launch faster without sacrificing security.
Compliance and Regulatory Alignment
Compliance is a critical element of web app security, especially for industries under strict regulatory scrutiny. At Savvycom, we stay ahead of regulatory changes across various sectors and ensure that our web app solutions are compliant with global and regional security standards, such as GDPR for data privacy in Europe, HIPAA in the healthcare industry, and ISO/IEC 27001 for information security management.
By embedding compliance checks into our security audit processes, we help businesses avoid the legal and financial repercussions of non-compliance. This focus not only protects organizations from external threats but also ensures internal governance policies are strictly adhered to.
Get in touch with Savvycom for a free consultation. We’ll help you decide on next steps, explain how the development process is organized, and provide you with a free project estimate.
Scalable, Future-Proof Security Strategies
In today’s dynamic digital landscape, security measures must be able to scale as your business grows and technology evolves. At Savvycom, we adopt a future-proof approach to web app security, ensuring that your application can handle not only current threats but also adapt to future vulnerabilities. Our solutions are built to be scalable, enabling businesses to expand their digital presence securely, whether through cloud migrations, API-driven architectures, or microservices.
Our deep expertise in emerging technologies like blockchain, AI, and IoT security allows us to anticipate security challenges associated with new tech trends. This proactive mindset means that as your business adopts new innovations, our security frameworks evolve to mitigate risks before they materialize.
Expert Security Consultation and Support
What sets Savvycom apart is not just the technology we implement but the expert guidance we provide. Our team of cybersecurity professionals collaborates closely with clients to understand their unique risk profiles and security goals. We offer security consultation services that help businesses assess their current defenses, identify gaps, and design comprehensive strategies that go beyond compliance to achieve maximum security resilience.
In addition, we provide ongoing support and maintenance, ensuring that your security infrastructure is regularly updated to protect against new vulnerabilities and comply with evolving regulatory standards. This means you can focus on innovation and growth while knowing your web applications are secured by trusted experts.
FAQs
How often should web applications be updated for security?
Web applications should be updated regularly, especially after new vulnerabilities are discovered. Automated tools can help detect and apply necessary patches faster.
What tools can I use to monitor my web app for vulnerabilities?
Tools like Burp Suite, OWASP ZAP, and Acunetix are popular choices for vulnerability scanning and penetration testing.
How does Savvycom help with web app security?
Savvycom offers end-to-end web app development and cybersecurity outsourcing services that ensure your web applications are secure, scalable, and compliant with the latest standards.
Conclusion
Web app security is a critical aspect of modern business operations. As web apps become increasingly complex, securing them requires a multi-faceted approach that combines authentication, encryption, input validation, and security automation. By staying informed about emerging threats and partnering with experts like Savvycom, businesses can safeguard their web applications against the growing threat landscape of 2025.
Savvycom, as a leading software development company, specializes in developing secure and robust web app development services tailored to your business needs. We also offer a comprehensive range of cyber security outsourcing services to safeguard your business against evolving cyber threats. As one of the top cybersecurity companies, we specialize in diverse types of cybersecurity strategies tailored to meet the unique needs of each client. Our cybersecurity services include Professional Services such as Penetration Testing, Red Team operations, Incident Response, and Digital Forensics, as well as Managed Services including Security Operation Center (SOC), Network Operation Center (NOC), and Application Managed Service. From cybersecurity risk assessments to advanced cyber threat management, we ensure robust protection for your critical assets. Contact us to learn how we can help you protect your web app from current and future threats.


